 Anticipate business risks and minimize potential damage
Anticipate business risks and minimize potential damage
Anticipate business risks and minimize potential damage
Anticipate business risks and minimize potential damage
Risk management involves anticipating potential future risks and implementing measures to minimize the impact if those risks materialize. It is an critical practice for organizations to maintain stable economic and business operations.
What is Risk Management?
Risk management is the process of anticipating risks that may occur in the future and taking measures to minimize the impact if they do occur.
In the context of information security, risk management begins with identifying threats that could affect the information assets to be protected and evaluating the potential impact if those threats materialize (risk assessment). Based on the level of impact, appropriate controls are then implemented to minimize the risks.
Risk management is not something that can be completed with a one-time effort. In the field of information security in particular, if you are not continuously and proactively implementing measures, you will not be able to respond to new threats as they emerge. As the environment changes, ongoing review and improvement are required.
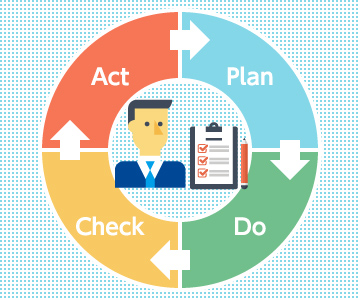
To continuously maintain and improve the level of achievement of security objectives within an organization, the PDCA cycle—Plan (planning), Do (implementation), Check (inspection/audit), and Act (review/improvement)—must be repeated on an ongoing basis.
Asgent provides a variety of support services to help organizations implement effective risk management, including:
- Preparing for audits or establishing an audit framework
- Preparing for audits or establishing an audit framework
- Achieving certification compliance
Two Key Featues of Asgent’s Risk Management
-
Support from Auditors’s Experienced in Audit Operations
To implement effective risk management, it is essential to establish the right internal framework. Asgent’s auditors, who have a strong track record in conducting information security audits for a wide range of organizations—including government agencies, financial institutions, and service industries —help you build that framework through activities such as internal audits and support for certification acquisition.
Our auditors’ expertise is recognized in source such as the FY2017 “Information Security Audit Company Registry”.
-
2 Support Tools for Effective Risk Management
We provide tools that support effective risk management. While people ultimately play the most important role in risk management, organizations lacking sufficient expertise can achieve standardized and consistent measures by leveraging these support tools.

Services and Products Overview
| Object | Services and Products | |
|---|---|---|
| Prepare for audits / Establish an audit framework | ServiceInformation Security Audit | |
| Strengthen security governance | ProductsM@gicPolicyCoSMO | |
| Obtain certifications | ServiceObtain certifications | |
| ServicePrivacyMark Consulting | ||
| ServicePCI Data Security Standard Consulting |
