 Strengthening Security for Public Cloud Environments
Cloud Security
Strengthening Security for Public Cloud Environments
Cloud Security
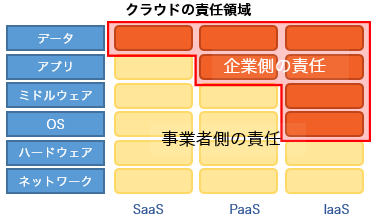
As the phrase “Cloud First” suggests, many IT departments are already migrating, or considering migrating, a large portion of their information assets to the cloud. By moving to the cloud, organizations can provision server and network infrastructure without building it in-house, deploy required systems quickly and at lower initial cost, and reduce total cost of ownership. However, even with the cloud services, it is essential to understand the shared responsibility model and implement appropriate security measures. In particular, in the case of IaaS in public cloud environments, responsibility for the OS running on the hardware, databases, applications, and account management lies with the customer organization.
Security Requirement for the Public Cloud Environments
-
Protection Against the Latest Cyber Attacks
Most cloud providers offer their own security features. However, these are typically provided on a per-service or per-function basis and differ from the measures offered by dedicated security vendors. As a result in several challenges, they may not be sufficient to deal with the latest threats such as zero-day attacks, and in many cases, analyzing logs requires combining multiple services. For these reasons, it is necessary to deploy additional security controls for public cloud environments, just as you would for on-premises systems.
◆ Key Security Measures Provided by Cloud Service Providers and Their Limitations
Security Services Provided Challenges Access Control (IP address–based) ・Inability to perform Deep Packed Inspection (DPI)
・Lack of granular packed inspection capabilities
・The current infrastructure provides limited visitiity into payload-level dataWeb Application Firewall ・Lack of support for non-Web protocols
・Inability to detect outbound communication to Command and Control (C&C) servers upon server compromiseLog Analysis (Optional Add-on) ・Log storage and analysis are separate and charged on a usage basis according to data volume (additional costs incurred)
・Log analysis using only standard services requires specialized expertise and the integration of multiple services -
Visualization of Security Configurations
While the adoption of public cloud services continues to accelerate, information security incidents caused by misconfiguration and human error are also rapidly increasing. It is no longer uncommon to see data breach cases where, due to incorrect permission settings in a cloud service, customer information that should never have been accessible was unintentionally exposed. Even if the initial configuration is appropriate at the time of deployment, security vulnerabilities can emerge over time due to various factors—such as accidental errors during later configuration changes, inappropriate operations caused by lack of knowledge, or the neglect of obsolete resources, Furthermore, as public cloud usage grows and the scale of provided and consumed services expands, it becomes increasingly critical to maintain an accurate view of configuration settings across diverse resources and to manage permissions for all accounts in order to preserve security.
-
Strengthening the Information Security Management Frameworks
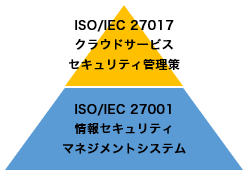
Across all environments - including cloud, hosting, ASP, and on-premises - , it is critical to cover the fundamentals of security. In practice, this means aligning with the organization’s information security strategy and policies, classifying information assets and data according to their importance, and then designing access controls, operational processes, and incident response structures that match each level of importance. ISO/IEC 27017 is a guideline standard that defines information security controls for cloud services. By reinforcing an existing ISO/IEC 27001–based information security management system with ISO/IEC 27017, organizations can build a robust information security management framework that properly addresses cloud services as well.
Asgent’s Services and Product Portfolio
| Scope of Products | Products /Services | Overview |
|---|---|---|
| Protection against the latest cyber attacks | Product Check Point CloudGuard Network |
Provide a defense-in-depth architecture specifically designed for cloud infrastructure. By comprrementing the native security features offered as standard by cloud providers, our product delivered robust, next-generation firewall capabilities. This includes advanced sandboxing to detect unknown malware and file sanitization. |
| Service Security Plus Managed Security Service |
Addresses the critical challenges faced by organizations lacking in-house security expertise, where log analysis and responding to sophisticated cyberattacks can be complex and demanding. Security devices running in cloud environments are monitored 24/7/365 by Asgent’s dedicated security analysts. |
|
| Visualization of security settings | Service Security Plus Security Assessment Services : Web Application Assessment |
To maintain a secure posture for system exposed to the cloud, we identify the presence of underlying security flaws (vulnerabilities) This service meticulously inspects and detects vulnerabilities latent within your web applications. Our engineers examine and identify vulnerabilities in your web applications. After the assessment, we provide a detailed, easy-to-understand report and explain the findings and recommend next steps. |
| Service Security Plus Security Assessment Services : Platform Assessment |
Clarifies whether security issues (vulnerabilities) exist in systems published on cloud environments, helping maintain their security posture. We examine and identify flaws (vulnerabilities) in servers, network devices, operating systems, and middleware. Upon completion, we deliver comprehensive and intuitive reports, providing detailed findings alongside strategic recommendations for effective remediation. |
|
| Strengthening the information security management framework | Service Information Security Audit |
Supports the development of an internal framework that enables the organization to understand the status of information security measures for its information assets and to identify issues that need to be addressed. |
| Service ISO Consulting |
Provides expert guidance onn building the internal frameworks and cloud-specific controls required for successful ISO/IEC 27017 certification. |
