 Conduct security vulnerability assessments of the current websites
and internal networks.
Security Assessment (Vulnerability Assessment)
Conduct security vulnerability assessments of the current websites
and internal networks.
Security Assessment (Vulnerability Assessment)
Attacks that exploit vulnerabilities in operating systems and applications are occurring with increasing frequency, and information leakage resulting from unauthorized access and targeted attacks continue to pose a serious threat.
Understanding the current state of systems to determine whether vulnerabilities exist, and implementing improvements based on the assessment results, is essential to strengthening overall security measures.
About Security Assessment
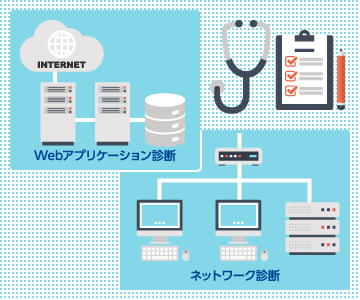
Security assessments conducted to identify the presence of vulnerabilities generally fall into two categories: “Platform Assessments” and “Web Application Assessments”.
A platform assessment examines servers, network devices, operating systems, middleware and related components to identify vulnerabilities, configuration flaws within web applications.
Assessment methodologies include tool-based assessments and manual assessments performed by security consultants and engineers. Manual assessments are particularly effective in identifying vulnerabilities and weaknesses that are difficult to detect using automated tools alone.
In addition, a Penetration Test – also referred to as an intrusion test – is conducted to evaluate the effectiveness of existing security controls by determining whether specific attack objectives can be achieved through simulated attacks. Penetration testing is often employed as part of broader security assessment and investigation activities.
During a penetration test, realistic attack scenarios that would likely to be used by actual attackers are developed, and simulated attacks are executed accordingly. This approach evaluates not only the existence of vulnerabilities, but also post-compromise behavior and the presence of sensitive or high-risk information assets, providing an attacker’s eye view of the organization’s security posture.
The Importance of Security Assessments
Incidents caused by attacks that exploit system vulnerabilities – such as personal information leakage, website defacement, system outages, service disruptions and system being abused as attack footholds – continue to occur. When such incidents arise, organizations may incur substantial costs, including expenses related to root cause analysis and remediation, compensation for affected individuals in the event of data breaches, downtime-related losses, reputational damage and loss of trust from business partners, and, in some cases, penalties for non-compliance with regulatory requirements. To migrate these risks, it is essential to proactively identify and assess vulnerabilities that could be exploited by attackers.
In addition, eliminating vulnerabilities as sources of concern provides significant value for services offered to customers, enabling end users to utilize those services with confidence. In recent years, we have increasingly received inquiries from web application development companies whose customers require third-party vulnerability assessments as a condition for system delivery, highlighting the growing importance of security assessments as a standard business requirement.
Differences Between Vulnerability Assessment and Penetration Testing
With the growing awareness of information security in recent years, demand for these types of assessments has increased significantly. However, the terms “penetration testing” and “vulnerability assessment” are often used interchangeably by assessment providers. As a result, there are frequent cases in which penetration testing is requested even though a vulnerability assessment would be more appropriate or vice versa.
When considering the assessment of systems to ensure they are not exposed to attacks, it is important to determine whether a vulnerability assessment or a penetration test is more suitable for your objectives. Please refer to the following overview to help guide your decision.
| Vulnerability Assessment | Penetration Testing | |
|---|---|---|
| Purpose | Comprehensively identify vulnerabilities and deficiencies in security controls | Verity whether a threat actor with clear intent can successfully achieve their objectives |
| Scope | Per specified web applications or IP addresses | Target systems, personnel, organizational structures, and policies, covering either all systems owned by the organization or specified systems |
| Methodology | Examine system components against security standards and best practices | Conduct simulated attacks to evaluate whether defined objectives can be achieved within a specified timeframe |
| Reporting and Deliverables | List of identified vulnerabilities and security control gaps | Results of attack scenario validation |
Appropriate Timing for Vulnerability Assessments
Organizations that meet any of the following criteria are strongly advised to promptly conduct a vulnerability assessment, as security products alone cannot eliminate all vulnerabilities.。
- Organizations operating websites that have been publicly accessible on the Internet for an extended period without having undergone a vulnerability assessment
- Organizations that have not conducted a vulnerability assessment due to reliance on security products, but have developed concerns about their overall security posture after reviewing security risks.
Organizations that fall under any of the following conditions are advised to conduct a vulnerability assessment prior to public release, considering the remediation period required after the assessment.
- The website has been newly developed, enhanced, or modified, and there is a need to identify vulnerabilities and security risks before release
- Internal policies require vulnerability assessments to be conducted on a regular basis
- Project security requirements mandate a third-party vulnerability assessment prior to delivery
- Secure programming practices have been implemented based on guidelines, but there is a need to verify that they are being applied correctly
When a website is newly developed, expanded, or modified, it is strongly recommended to conduct a vulnerability assessment before it is made publicity accessible on the Internet. In addition, as new attack techniques continue to emerge daily, we also recommend performing a regular assessment of the entire website, typically once per year.
For site expansions or modifications, risks can be significantly reduced by limiting the assessment scope to the modified components and any areas affected by those changes.
In practice, we often receive inquiries such as:
- “The website does not store personal information, so a vulnerability assessment was not conducted, however, it was later requested by a
business partner as part of supply chain security measures”, or.
- “An assessment was performed once before the service launch, but several years have passed since then, and concerns were raised by customers.”
In many cases, vulnerability assessments reveal a significant number of high-risk vulnerabilities. Ideally, a vulnerability assessment should be conducted once prior to public release, followed by annual periodic assessments thereafter.
Security Level Assessment by Asgent: Three Key Features
-
Vulnerability Assessment by Experienced Security Engineers
Our experienced security engineers assess systems from an attacker’s perspective, reflecting business requirements and system specifications, and addressing the latest attack techniques based on up-to-date threat intelligence. -
Tailored Assessment Methods Optimized for Each Customer
Asgent offers a wide range of vulnerability assessment services, from automated tool-based testing to in-depth manual assessments. Asgent’s engineer proposes the most appropriate assessment approach based on each customer’s budget and security requirements.
For both automated and manual assessments, experienced security engineers conduct a formal results briefing based on the assessment report and provide clear recommendations for remediation and next steps, ensuring confidence and transparency throughout the process. -
Security Solution Recommendations After Vulnerability Assessment
While many assessment services provide remediation guidance in their reports, identifying and selecting appropriate security solutions can be time consuming. Asgent offers a broad portfolio of security products and services and can recommend optimal security solutions to effectively mitigate the vulnerabilities identified during the assessment.
Services and products
- Asgent’s security assessment (vulnerability assessment) services include free initial consultation and quotation. Please feel free to contact us.
