Penetration testing by security experts to evaluate access and post-breach risks
Penetration Test
Penetration testing by security experts to evaluate access and post-breach risks
Penetration Test
A penetration test involves our security specialists conduct simulated attacks on your information systems, attempting to penetrate them in the same way an attacker would in order to achieve their objectives.
By performing a penetration test, organizations can identify inherent system vulnerabilities, verify whether an attacker’s objectives can be achieved through simulated attacks, and evaluate the effectiveness of your current security measures.
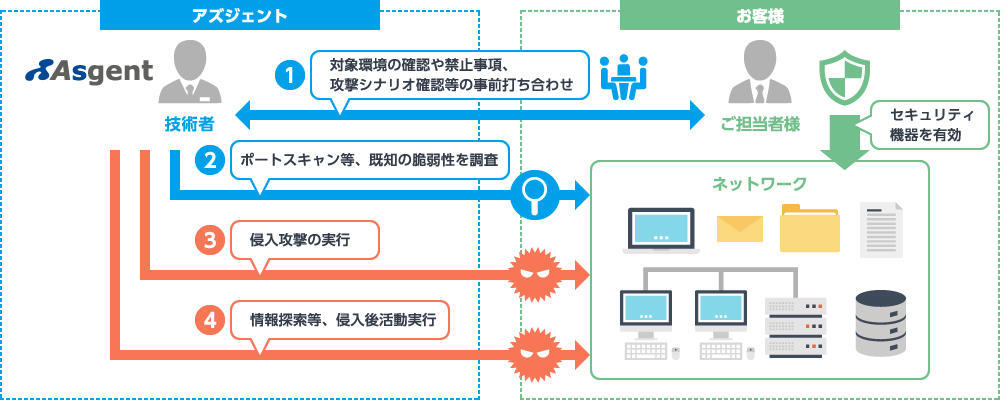
The impact and information that can be obtained differ depending on the attack techniques used in a penetration test.
Therefore, it is important that our specialists first conduct a thorough interview about your environment and agree with you on the scope of the test in advance. This enables us to design and execute the most appropriate attack scenarios for your organization.
In addition, during the post-test reporting session, recommendations for countermeasures are provided, helping to enhance the security level of the customer’s information systems.
Features
-
Investigation, Verification, and Countermeasure Recommendations by Experienced Specialists
Our experienced security specialists conduct inspection of the customer’s systems. After the assessment, we hold a review session where we explain the results (presence or absence of vulnerabilities, descriptions of threats, etc.) and present recommended countermeasures. -
Flexible Support Tailored to System Environments and Business Requirements
System objectives and requirements vary by customer—for example, e-commerce sites and member-only services. Preliminary consultations are conducted to propose the most appropriate investigation and testing approach for each customer.
Benefits
-
Enhancing Security Level
By addressing the risks identified through the penetration test, you can enhance the overall security level of your systems. -
Proactive Assessment of Potential Damage
Penetration testing allows organizations to anticipate what kind of damage could occur if existing vulnerabilities were exploited. It also enables you to verify the effectiveness of your current cybersecurity measures.
Service Flow

Investigation Example
Assuring a malware infection scenario, the assessment evaluates potential impacts and determines whether sensitive information could be compromised.