 Strengthening the security of websites against diverse cyber threats
Web Security Countermeasures
Strengthening the security of websites against diverse cyber threats
Web Security Countermeasures
Today’s web servers are exposed to a variety of threats that cannot be mitigated by traditional firewalls alone. In other words, simply deploying a gateway device does not mean that countermeasures are complete. There is a growing need to address latent vulnerabilities within running applications, to maintain an equal or higher level of security across diverse environments such as cloud and virtual infrastructures, and to protect web servers at the application layer.
What Are Web Security Countermeasures?
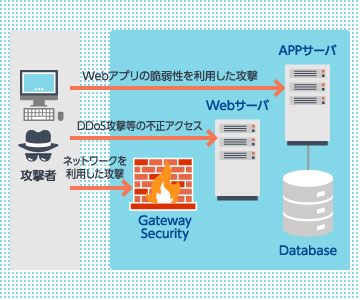
Websites and web applications that your organization builds and operates are constantly exposed to various external threats. Typical examples include attacks that exploit vulnerabilities to break into internal systems and cause information leaks or website defacement, as well as denial-of-service (DoS) attacks that forcibly disrupt business operations from the outside. By their very nature, websites and web applications require ongoing security measures. If attacks result in website defacement or information leaks, the consequences—such as damage to your brand and loss of trust, or even liability for damages—are clearly unacceptable.
Asgent’s web security solutions provide a comprehensive range of services, including assessments to determine whether customers’ websites are adequately protected against external threats, vulnerability assessments of servers, software, and web applications, and services that defend live websites against DoS attacks.
We propose the optimal r web security framework.
- Protecting websites from cyberattacks
- Identifying and assessing vulnerabilities in your website
Three Key Features of Asgent’s Web Security Solutions
-
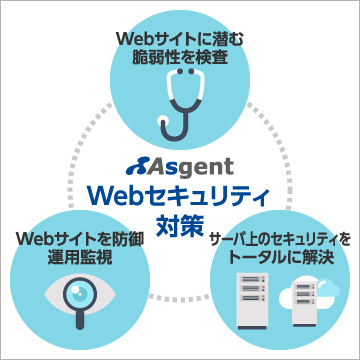
Assessing Vulnerabilities Embedded in Existing Websites
Web applications are commonly exposed to a wide range of security issues, including SQL injection, OS command injection, and cross-site scripting, among many other known attack methods. Although these are security risks that should be addressed at the application level, insufficient countermeasures often lead to website defacement and information leaks.
By performing vulnerability assessments before a website goes live or on a regular basis, it is possible to check and report whether your website has adequate security measures in place. -
Easily Protecting Websites from DDoS Attacks and Defacement with Continuous Operations and Monitoring
Ideally, web applications would always be kept free of vulnerabilities, but achieving this in practice involves many challenges. DDoS protection can also be difficult to implement, as it may require substantial cost or significant changes to network architecture depending on the environment. Furthermore, establishing and maintaining a 24/7/365 monitoring capability – where security specialist continuously observe attack activity and respond appropriately is highly demanding.
By leveraging a SaaS-based WAF (Web Application Firewall) to keep your website protected in an always-optimized state, and combining it with expert incident monitoring, initial response, and security reporting services, you can effectively protect your websites from attacks. -
Comprehensive Server Security Across Virtual, Cloud, and Physical Environments
In recent years, the adoption of highly scalable public cloud services at relatively low cost has become widespread. However, when it comes to security, the responsibilities of the cloud provider and those of the user differ from traditional on-premises environments.
From the user’s perspective, key considerations include:
(1) Countermeasures in the event of security breaches at the virtualization layer
(2) Flexible security functions on virtual hosts
(3) Security measures that can scale in line with cloud environments
These considerations apply equally to virtual environments where servers are managed in-house. By implementing security solutions that support on-premises, cloud, and virtual environments, you can strengthen server security across all platforms.
Services and Products Overview
| Objective | Products and Services | |
|---|---|---|
| Protecting against attacks that exploit vulnerabilities | ServiceWebsite Protection Service | |
| ServiceMSS for Deep Security | ||
| ProductDeep Security | ||
| ProductCloud Application Protection Services | ||
| Protecting against DDoS attacks | ServiceWebsite Protection Service | |
| ProductCloud DDoS Protection Services | ||
| Finding out whether vulnerabilities exist | ServiceWeb Application Assessment Service |
