 Host-based server security solution to address security challenges across virtual, cloud and physical
Trend Micro Deep Security
Host-based server security solution to address security challenges across virtual, cloud and physical
Trend Micro Deep Security
Trend Micro Deep Security (Deep Security) delivers the key capabilities required to protect servers, including IPS/IDS, firewall, change monitoring for files and registries, security log monitoring, and anti-malware. By utilizing agents and virtual appliances, it provides integrated server security across physical, virtualized and cloud environments.
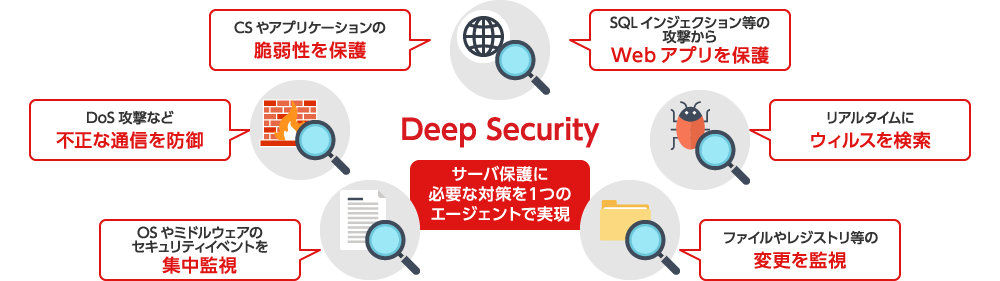

Key Features of Trend Micro Deep Security
-
Protect Servers with Agent-Based and Virtual Appliance Modules
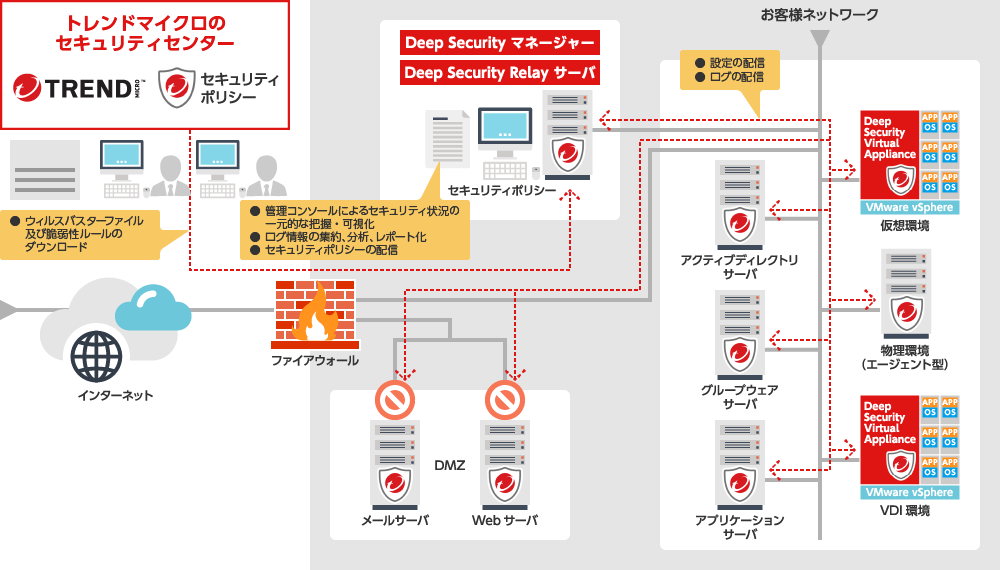
Deep Security protects physical servers, virtual environments, and cloud environments through agent-based (host) and Vitrual Appliance -based protection modules, providing security measures tailored to each environment. Because all protection modules are software-based, there is no need to change your network architecture when deploying. You can install only as many modules as you need, on the servers that require protection. All of these modules are centrally managed by the Deep Security Manager, allowing you to enforce unified security policies across your entire server environment.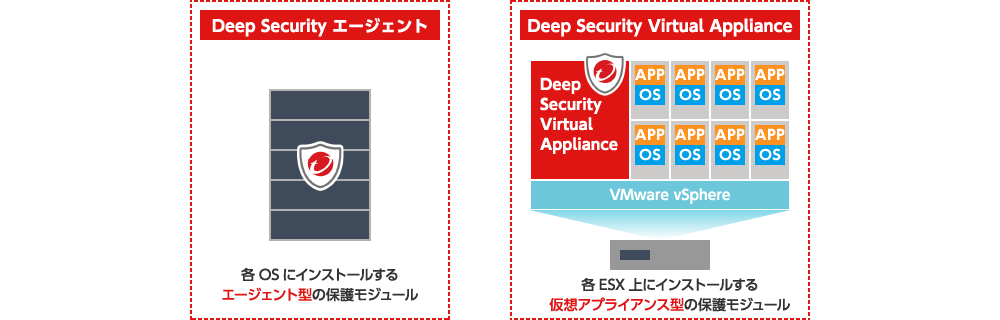
-
Protect Critical Servers with Six Essential Security Functions
Deep Security provides the following six capabilities required for robust server security. From the network layer up through the operating system and application layers, it enables true multi-layered protection for your servers:
■Anti-Malware with Web Reputation
■Web Application Protection
■Intrusion Detection and Prevention (Host-based IDS/IPS)
■Firewall
■File and Registry Integrity Monitoring
■Security Log Monitoring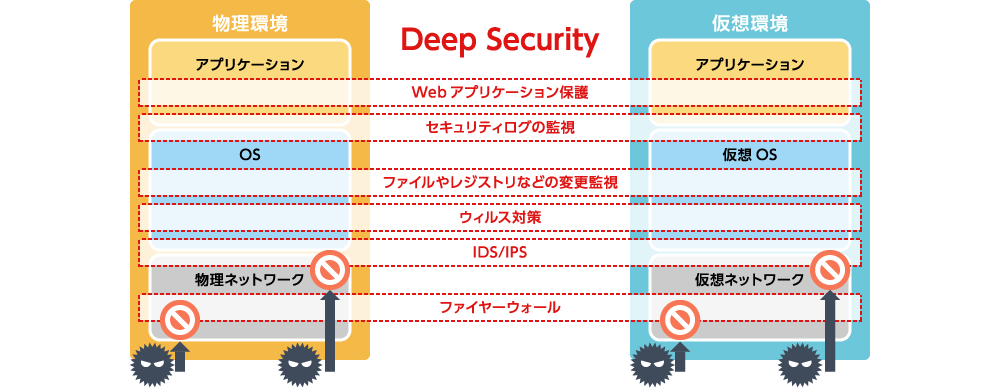
-
Support for a Wide Range of Server OS
The Deep Security Agent supports major server operating systems, including Windows, Linux, and Solaris. For Linux, it covers five major distributions: Red Hat, SUSE, CentOS, Ubuntu, and Amazon Linux. In addition, Deep Security can protect against vulnerabilities in more than 100 applications running on top of these operating systems. In today’s environment, where managing security workloads is a major challenge, Deep Security provides an optinal solution for protecting mixed IT environment.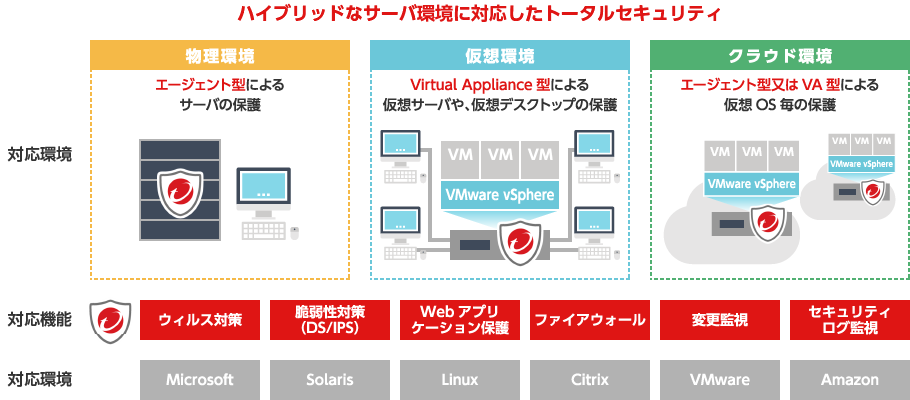
Product Lineup
| Deep Security Agent | The Deep Security Agent is a software-based protection module installed directly on the operating system.It supports major server OSs such as Windows, Linux, and Solaris, and provides six key security capabilities: • Anti-malware • IDS/IPS • Web application protection • Firewall • Integrity monitoring • Security log monitoring |
|---|---|
| Deep Security Virtual appliance | The Deep Security Virtual Appliance is a virtual appliance–type protection module installed on each ESX host. By intercepting network traffic and file I/O at the hypervisor level, it delivers: • Anti-malware • IDS/IPS • Web application protection • Firewall • File integrity monitoring without the need to install agent -based security software on individual virtual machines. |
| Deep Security Manager | Deep Security Manager is the central management server for all Deep Security protection modules (agents and virtual appliances). It distributes configurations to protection modules and centrally stores detected events and logs. The manager can be configured for high availability; protection modules automatically recognize redundant managers and switch communication to be the secondary server if the primary goes down. Even if both managers fail, the protection modules continue to operate independently, ensuing uninterrupted security. |
| Deep Security Relay | Introduced in Deep Security 8.0, the Deep Security Relay component is a dedicated server that distributes security rules—such as virus definition files and vulnerability rules—received from Trend Micro’s Security Center to all protection modules In small environments, the Relay can be co-located with the Deep Security Manager. In larger environments, multiple Relay servers can be deployed to distribute updates and reduce the load on individual servers. |
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
