 Sophisticated cyberattacks and security measures in the era of hybrid work
Zero Trust
Sophisticated cyberattacks and security measures in the era of hybrid work
Zero Trust
Cyberattacks targeting organizations are increasing year by year, and the methods used are becoming more sophisticated.
With the rise of remote work, cloud adoption, and the widespread use of SaaS, both the locations of connected devices and the destinations of accessed data are becoming more diverse. In this context, the concept of "zero trust" has emerged as a key framework for modern security strategies.
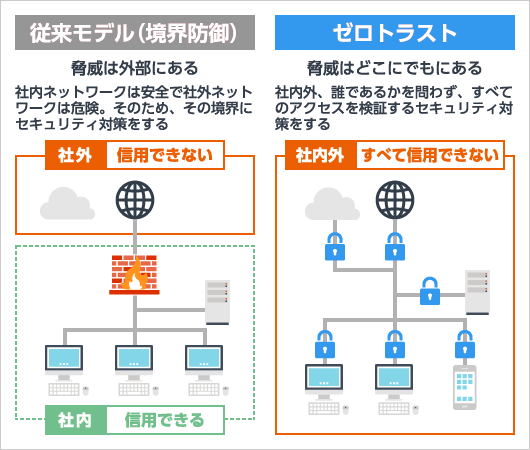
What is zero trust?
In the zero-trust model, security threats are recognized not only on external networks but also within internal networks, and all entities attempting to access protected internal resources are traated as untrusted and must be verified. The traditional perimeter-based security model assumes that critical information assets reside inside a defined boundary and that threats come from outside that boundary. However with the growing adoption of cloud services and the diversifications of working environments, such as remote work, the boundary separating internal and external networks has become increasingly ambiguous, rendering conventional measures insufficient. In this context, the zero trust approach has gained significant attention as a more effective security paradigm.
Advantages and Challenges of Zero Trust
・Support diverse workstyles while ensuring security
By implementing zero trust security, organizations can continuously verify the security if uses an device regardless of whether they are accessing from inside or outside the cooperate network, enabling safe and reliable access to internal resources. The same authentication can be applied not only to company-issued devices but also to personally owned devices, enabling secure BYOD.
・Secure use of cloud services for business operation
Since communications to cloud services are also subject to inspection, access to cloud services is strictly verified and authenticated regardless of who is accessing them or from where. Even if you were previously hesitant to use cloud services due to security concerns, zero trust makes it easier to use them with confidence in business environments.
・Integrated security management and improved operational efficiency
In traditional perimeter-based security models, each security appliance typically had to be configured individually during deployment and operation, often resulting in complex settings.
In contrast, zero trust security integrates multiple security functions in the cloud and applies the same strict authentication to all access, enabling more efficient operation and centralized management.
Challenges
・Higher costs and longer implementation time
A zero-trust network cannot be achieved by simply deploying a single solution. To realize zero trust, it is necessary to build an environment by combining multiple solutions and services, starting with authentication. As a result, migrating from a traditional perimeter-based model to a zero-trust network requires both time and cost.
・Potential impact on convenience
Zero trust enhances security by continuously verifying all access. As a result, even systems that users previously accessed without function will now require authentication, which may lead to a reduction in convenience in some cases.
Solutions for Implementing Zero Trust
Based on materials from IPA (Information-technology Promotion Agency, Japan), specifically the "Zero Trust Implementation Guide" and "Introduction to Zero Trust," the following are examples of solutions that help realize zero trust.
-
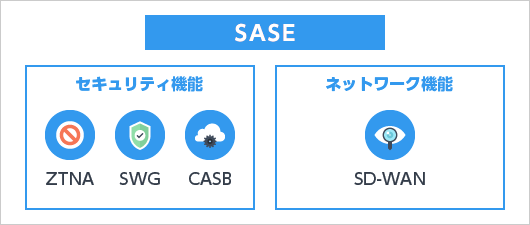
SASE
SASE (Secure Access Service Edge) is a concept that integrates network and security functions, traditionally provided separately, into a single cloud-delivered service. SASE is based on the zero trust principle that perimeter-based defenses designed only for internal environments are no longer sufficient now that work is no longer confined to the office. By enabling unified management network and security functions in the cloud, SASE addresses the challenge and can be considered an all-in-one service that allows secure system access regardless of the location of users or devices. - Main components of SASE
・ZTNA((Zero Trust Network Access)
This service controls user access at the application and data level in line with zero trust principles.
・SWG(Secure Web Gateway)
This service is primarily designed to protect providing functions such as web access control and traffic visibility.
・CASB(Cloud Access Security Broker)
This service provides centralized management by visualizing and controlling the use of all cloud services.
・SD-WAN(Software Defined Wide Area Network)
This service builds a virtual WAN on top of physical networks and uses software to monitor and control communications. - Check Point’s SASE solution, combining SWG and ZTNA, with a proven track record of adoption by more than 3,000 organizations worldwide
- Performs continuous authentication through detailed device policy checks
- Flexible licensing model, allowing deployment from as few as 10 users
-
EDR/EPP (Endpoint Security)
Under the zero trust model, communications from all endpoints such as PCs, servers, and mobile devices are not trusted by default and must be verified, regardless of whether they originate inside or outside the organization. EDR (Endpoint Detection and Response) is a solution designed to detect suspicious behavior on endpoints and enables rapid response to prevent the spread of damage. EPP (Endpoint Protection Platform) refers to solutions that detect and prevent malware infections, such as traditional antivirus. In many cases, EPP functions are included as part of EDR products.
ProductCheck Point Harmony Endpoint – Key Features
- Provides all-in-one package of endpoint capabilities, covering preventive measures against threats and unauthorized access protection, post-infection response and investigation, encryption, and endpoint management
- Automatically mitigates damage caused by ransomware through built-in self-healing functions
- Detects phishing sites using an up-to-date threat intelligence knowledge database
- Reduces operational TCO with a unified, comprehensive management console
Check Point
Harmony Endpoint
-
File Sanitization Solutions
The zero trust principle of "never trust, always verify" aligns closely with Votiro’s file sanitization solution which proactively prevents attacks by neutralizing all incoming files from external sources across various channels such as email and the web.
ProductThis is a new type of anti-malware solution that focuses on the possibility that files may contain malicious code or malware, and sanitizes (neutralizes) email attachments and files downloaded from the internet. Learn MoreVOTIRO Secure File Gateway

Check Point
Harmony SASE

