- “Harmony SASE Internet Access,” a Secure Web Gateway function that protects access to the internet
- “Harmony SASE Private Access,” a ZTNA function that enables secure access to internal resources from any user location based on zero trust principles.
Features of Harmony SASE
-
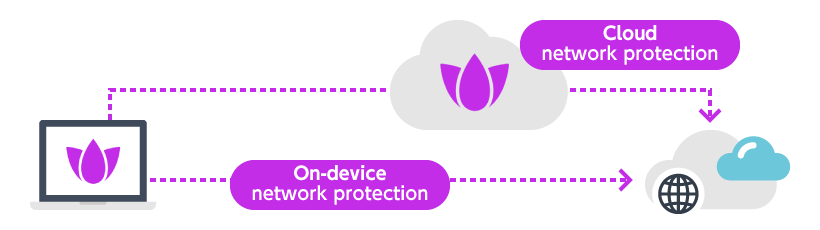
High-speed internet access with a hybrid architecture – Internet Access –
In typical SASE solutions, internet traffic is inspected by a secure web gateway running in the cloud, which often introduces latency and degrades the user experience. Harmony SASE Internet Access implements malware protection and URL filtering functions directly on the device agent, delivering up to twice the internet security performance compared to conventional solutions.
-
Full-mesh connectivity that secures access to all resources – Private Access –
Harmony SASE Private Access protects access to resources both on-premises and in the cloud using zero trust policies.
Through a single, intuitive dashboard, you can easily configure connections between cloud networks and connectors used for site-to-site connectivity, enabling you to build a zero trust network—typically considered complex—in a short amount of time.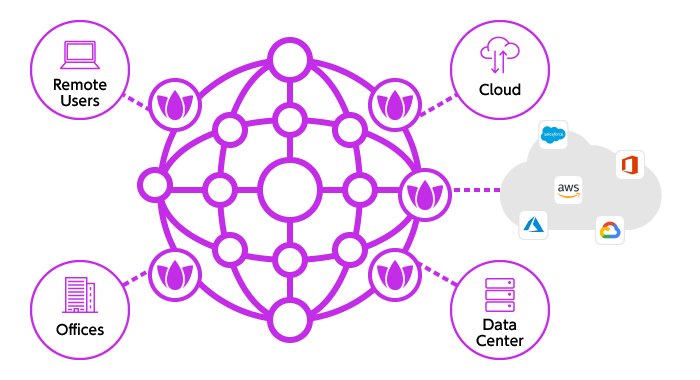
-
Granular device posture checks – Private Access –
In the zero trust model, authentication and continuous authorization are essential. Harmony SASE Private Access performs detailed device posture checks when connecting to internal resources and at defined intervals, monitoring the state of client devices to enforce strict access control.

-
Licensing available from as few as 10 users
Harmony SASE licensing has a simple structure: licenses for dedicated gateways deployed in the cloud, plus user licenses available starting from a minimum of 10 users. This makes it easy for small and mid-sized organizations to begin their transition to a zero trust network.
The minimum number of users may vary depending on the functions used. Please contact us for details.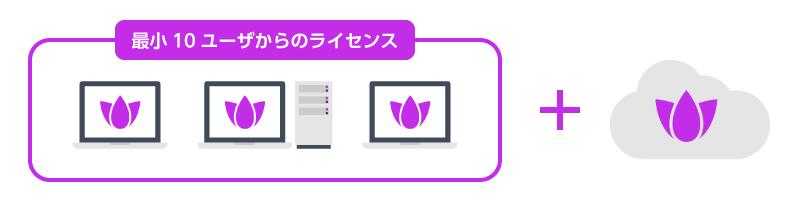
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
 Delivers network security with an optimal user experience
Delivers network security with an optimal user experience