 Preparing for Advanced Persistent Threats (APTs) requires the implementation of a holistic, multi-layered security framework
Countermeasures Against Targeted Attacks
Preparing for Advanced Persistent Threats (APTs) requires the implementation of a holistic, multi-layered security framework
Countermeasures Against Targeted Attacks
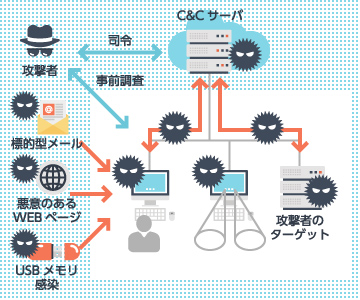
A targeted attack does not refer to a single attack technique. Rather, it encompasses a series of persistent and sophisticated attacks carried out with strong intent, in which adversaries continuously employ multiple methods until their objectives are achieved.
A primary example involves cyberattacks that infiltrate a target organization’s network through diverse vectors – such as email, social media, or malicious websites – to exfiltrate sensitive data. However, thwarting a single attack vector does not end the threat; the adversary will simply pivot to another method. This necessitates proactive preparation for the next evolution of the attack. Consequently, defending an organization against such targeted threats requires more than isolated security measures. It demands a “Defense-in-Depth” strategy – a multi-layered architecture that integrates countermeasures for u known threats with early detection capabilities to identify anomalies at their onset.
Defense Against Targeted Attacks
Targeted attacks are cyberattacks directed at specific enterprises or organizations. While often motivated by the exfiltration of high-value financial data, we increasingly observe attacks driven by ideological agendas – such as those by “Anonymous” – where targets are selected for conflicting with the attackers’ principles or perceived sense of justice. These attacks are highly diverse in nature and extremely persistent, which adversaries employ a wide range of tactic repeatedly until their objectives are achieved. Common methodologies include “Spear Phishing” which exploits social engineering, and “Watering-Hole” attacks that deliver malicious payloads through compromised websites.
Because these sophisticated attacks evolve until they succeed, relying solely on “Perimeter Defense” (such as Firewalls or IPS) is inherently insufficient for total prevention. To build true resilience, organizations must move beyond the perimeter, implementing a multi-layered security posture that integrates defensive measures throughout the entire attack lifecycle.
Asgent provides comprehensive Defense-in-Depth strategies by integrating a diverse portfolio of products and services. Our approach ranges from perimeter defense, which blocks suspicious traffic, to proactive countermeasures against unknown threats and specialized CSIRT establishment support. By orchestrating these multiple layers of protection, we deliver a robust security posture capable of thwarting today’s most sophisticated attacks.
We offer a strategic framework to fortify your security posture:
- Proactive Prevention and Mitigation: Detect early signs to neutralize threats and minimize impact.
- Counter Unknown Threats: Deploy advanced protection against zero-day exploits.
- Rapid Detection: Instantly identify malware infiltration and attack traces.
- Targeted Attack Countermeasures for Ransomware Defense
In recent years, ransomware has become one of the most pervasive and damaging cyber threats. This category of malware encrypts critical data, rendering systems inoperable, and subsequently demands a ransom in exchange for the restoration of access.
More recently, ransomware attacks have become increasingly sophisticated and malicious. In addition to data encryption, so called “Double Extortion” tactics have been observed, in which attackers exfiltrate data prior to encryption and threaten to publicly disclose it unless the ransom is paid. While ransomware was once dominated by high-volume, “spray-and-pray” email campaigns, the focus has shifted to “Targeted Ransomware”. Adversaries now exploit system vulnerabilities or compromised credentials to infiltrate networks and move laterally to infect servers and workstations – tactics epitomized by groups like LockBit and Conti. Consequently, effective ransomware defense is now inseparable from advanced anti-targeted attack strategies.
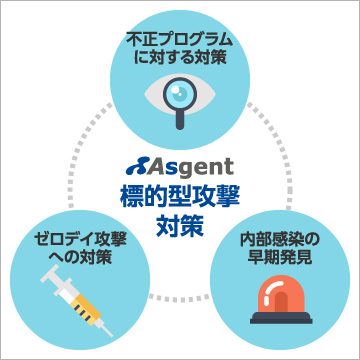
Asgent’s Targeted Attack Solutions: Three Key Pillars
-
Countermeasures against C&C Server Communications and Malicious Programs Including Bots and Ransomware
Since most targeted attacks infect host PCs to establish connectivity with a Command and Control (C&C) server – enabling attackers to hijack systems, laterally spread malware across the network, and exfiltrate sensitive data – it is imperative to implement traffic monitoring for early anomaly detection and proactive blocking of illicit communications based on the latest threat intelligence. -
Zero-Day Threat Mitigation
To effectively mitigate zero-day attacks, organizations should implement a framework that ensures safe data utilization by systematically vetting all files – whether received from external sources via email and social media or exchanged internally – through automated sanitization (Content Disarming) or risk assessment within a secure sandbox environment. -
Rapid Detection of Internal Infiltration
In contemporary targeted attacks, adversaries often remain latent within a network for extended periods to conduct reconnaissance, with the scale of damage typically correlating to the duration of this “dwell time”. To minimize actual loss, it is critical to maintain continuous monitoring of internal network traffic to detect suspicious anomalies, enabling rapid risk analysis and device identification to gain precise situational awareness and execute and immediate initial response.
Services & Products Portfolio: Comprehensive Overview
| Objective | Products & Services | |
|---|---|---|
| Early Detection of Attacks and Damage Mitigation | ServiceManaged Security Service | |
| ProductCheck Point Quantum Security Gateway | ||
| Countermeasures Against Unknown Threats | ProductCheck Point SandBlast TE Appliances | |
| ProductVotiro Secure File Gateway | ||
| Building and Operating a Moniroting System | ServiceSecurity Plus Managed Security Service |
Services & Products by Objective
Attack Detection and Damage Mitigation
Details
Security Plus
Managed Security Service

Details
Check Point
Quantum Security Gateway

Countermeasures Against Unknown Threats
Check Point
SandBlast TE Appliances

Details
Votiro Secure File Gateway

Building and Oprating a Monitoring System
Details
Security Plus
Managed Security Service

