As the “Cloud-First” paradium continues to gain momentum, many corporate IT departments are actively building new sustems or migrating existing legacy infrastructure to private and public cloud environments.
Check Point CloudGuard Network is a Next-Generation Firewall solution purpose-built for virtualized cloud infrastructures. Sharing the same proven architecture as Check Point’s on-premises gateways, it delivers robust, multi-layered security as a flexible virtual appliance.
Check Point CloudGuard Network is a Next-Generation Firewall solution purpose-built for virtualized cloud infrastructures. Sharing the same proven architecture as Check Point’s on-premises gateways, it delivers robust, multi-layered security as a flexible virtual appliance.
Features of Check Point CloudGuard Network
-
Public Cloud Security
-
Comprehensive Cloud Protection Powered by Software Blade Architecture
Check Point CloudGuard Network for Public Cloud enables organizations to secure servers and networks operating on platforms such as Amazon Web Services and Microsoft Azure.
This virtual appliance (a security gateway for virtualized environments) is designed for seamless deployment. It safeguards network connectivity within dynamic cloud computing environments, effectively preventing sophisticated attacks and data breaches. -
Inter-VM Traffic Inspection
With finely tunable Check Point firewall policies and industry-leading intrusion prevention capabilities, all traffic flowing between virtual machines—both internal and external—is inspected to protect the virtual machines. It secures virtual applications from external threats and enables isolation between them. Real-time updates keep your defenses always up to date. -
Unified management of physical and virtual environments
As with other Check Point security appliances, physical and virtual environments can be centrally managed using Check Point management products.
This ensures consistent security across all gateways while minimizing the cost associated with management consoles.
<Differences Between Host-Based security and Gateway-based Security (Check Point CloudGuard Network) in Public Cloud Environments> 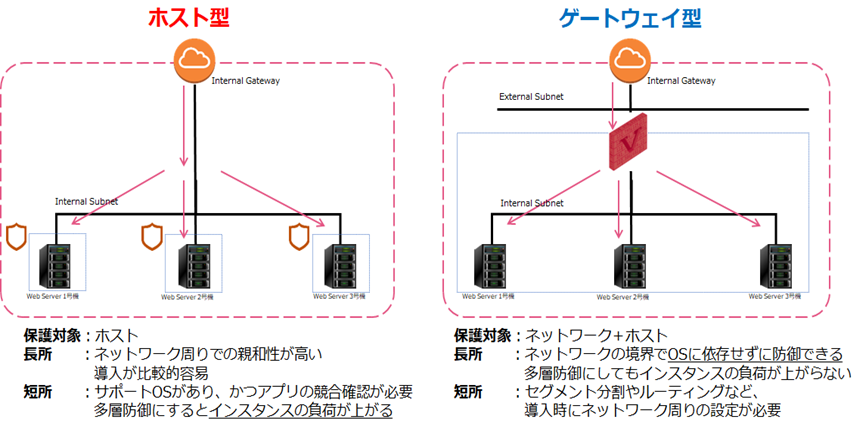
-
Comprehensive Cloud Protection Powered by Software Blade Architecture
-
Private Cloud Security
-
Comprehensive Protection for Cloud Environments with Software Blades
Check Point CloudGuard Network for private cloud security delivers advanced protection for east-west traffic within data centers by combining microsegmentation with a network virtualization platform that natively supports network isolation and segmentation. This approach enables granular security controls at the workloads level, significantly reducing lateral movement risks in cloud environment.
Unlike traditional architectures, CloudGuard eliminates the need for complex configurations involving VLANs, ACLs, firewall rules, physical firewalls, or router settings, thereby simplifying operations while strengthening the overall secusity posture of private cloud infrastructures. -
Enabling Multi-layered Defense Through a Single Virtual Appliance
Protection against sophisticated threats such as zero-day targeted attacks requires a multi-layered defense strategy rather than a single security control. Check Point CloudGuard Network integrates the essential security functions for zero-day attack prevention – malware protection (Antivirus, Threat Emulation, and Threat Extraction), vulnerability exploitation prevention (IPS), and data exfiltration prevention (Anti-Bot) – into a single virtual appliance. This unified approach delivers comprehensive multi-layered security while reducing deployment complexity, operational overhead, and overall cost. -
Seamless Delivery of Advanced Security
Check Point security gateway appliances are fully software-based and optimized using Intel CPU instructions without ASICs, delivering high performance even on virtual and cloud platforms. Enterprise-grade throughput starting from as few as 2 vCPUs, helping reduce operating costs on cloud platforms. As a higher throughput is required, performance can be increased simply by adding vCPUs.
-
Comprehensive Protection for Cloud Environments with Software Blades
Product Lineup
| Private cloud | Public cloud | ||
|---|---|---|---|
| Product lineup | for VMware NSX | for VMware ESXi | for Amazon Web Services for Microsoft Azure |
| License counting | Per physical CPU | Per virtual CPU | Per virtual CPU |
| Security functions |
Firewall IPsec VPN Identity Awareness IPS Application Control URL Filtering Anti-virus Anti-Bot Anti-Spam Content Awareness |
Firewall IPSec VPN Advanced Networking and Clustering Identity Awareness Mobile Access IPS Application Control URL Filtering Anti-Virus Anti-Bot Anti-Spam Content Awareness Threat Emulation Threat Extraction |
Firewall IPSec VPN Advanced Networking and Clustering Identity Awareness Mobile Access IPS Application Control URL Filtering Anti-Virus Anti-Bot Anti-Spam Content Awareness Threat Emulation Threat Extraction |
| Management functions | ─ |
Network Policy Management Logging and Status |
Network Policy Management Logging and Status |
For virtual environments other than those listed above, please contact us.
Licensing Procurement Example
Case Study: Licensing Check Point CloudGuard Network in NSX Environment
Assumptions: A total of 20 hosts (4 CPUs each) deployed in a VMware NSX environment
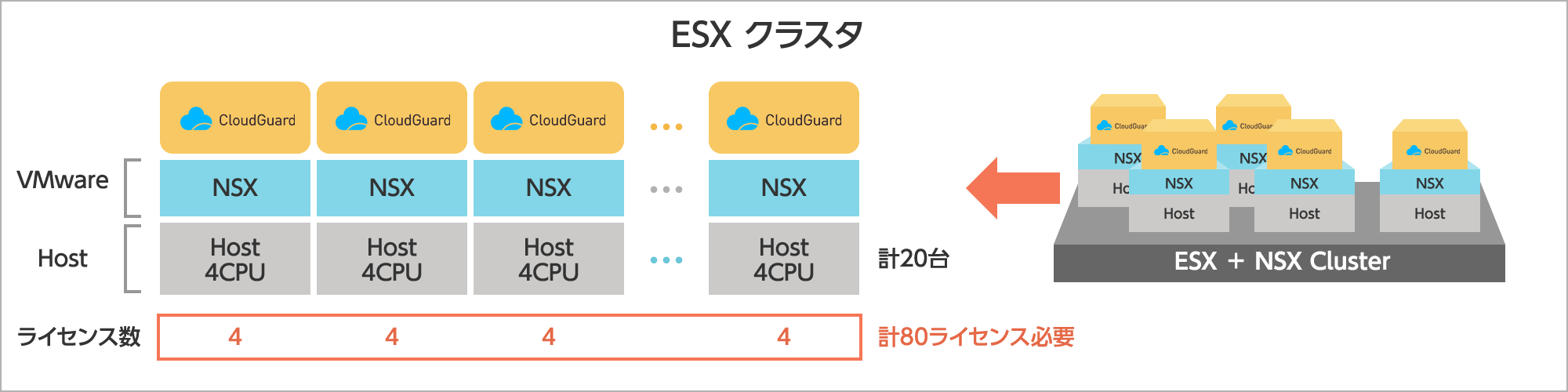
Case Study: Licensing Architecture in Check Point CloudGuard Netowrk for Tiered VE Gateway Offerings
A total of 120 vCores worth of licenses will be procured.
For low-end customers gateways configured with 2 vCores will be provisioned with gateways configured with 4vCores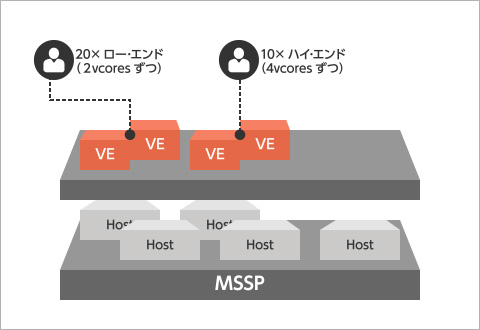
For low-end customers gateways configured with 2 vCores will be provisioned with gateways configured with 4vCores

[Current License Utilization Breakdown]
Low-end customers: 2 vCores × 20 customers = 40 licences
High-end customers: 4 vCores × 10 customers = 40 licences
In use: 80 licenses Unused: 40 licenses
Low-end customers: 2 vCores × 20 customers = 40 licences
High-end customers: 4 vCores × 10 customers = 40 licences
In use: 80 licenses Unused: 40 licenses
When adding more customers (10 low-end customers and 5 high-end customers)
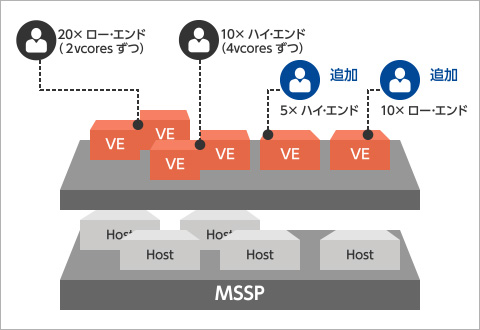

Low-end customers: 2 vCores × 20 customers = 40 licenses
High-end customers: 4 vCores × 10 customers = 40 licenses
In use: 80 licenses
Unused: 40 licenses
High-end customers: 4 vCores × 10 customers = 40 licenses
In use: 80 licenses
Unused: 40 licenses
In additional customers are onboarded in the future, the environment can be easy and flexibly scaled by purchasing additional licenses as needed.
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
 Next-Generation Firewall Solution that protects Public and Private Cloud Environments
Next-Generation Firewall Solution that protects Public and Private Cloud Environments