 A support tool designed to enable the efficient establishment and operation of ISMS and PMS
M@gicPolicyCoSMO
A support tool designed to enable the efficient establishment and operation of ISMS and PMS
M@gicPolicyCoSMO
Fully compliant with JIS Q 27001:2023 (ISO/IEC 27001:2022)
In recent years, it has become increasingly important for companies to fulfill their accountability from various perspectives, including compliance with laws and regulations such as the Act on the Protection of Personal Information, the Unfair Competition Prevention Act, and the J-SOX Act; business continuity management (BCM); and the improvement of customer services and safety.
Under the circumstances, the establishment and operation of information security management systems (ISMS) and personal information protection management systems (PMS) have become more important than ever as the infrastructure to meet these requirements. However, building an effective ISMS or PMS frameworks requires high level of expertise and time. This places a heavy burden on frontline security personnel and creates issues such as difficulty in operating and maintaining the ISMS or PMS after it has been built. M@gicPolicyCoSMO (Corporate Security Management Operator) is a tool designed to solve these issues and efficiently support the construction, operation, and maintenance of ISMS and PMS.
M@gicPolicyCoSMO was developed under the design supervision of Akihiko Komase, Fellow at Asgent Security Center, Asgent Inc.
M@gicPolicyCoSMO Features
-
Real-Time Work Through Centralized Data Management on A Server
M@gicPolicyCoSMO is an application installed and operated on a server within the organization. Each user accesses M@gicPolicyCoSMO via the intranet and can perform various tasks simultaneously. Because the results of each task are immediately reflected in the M@gicPolicyCoSMO database in real time, the administrative workload for aggregating, evaluating, and revising data updated by each department can be greatly reduced.
-
Full Support for All Phases of The PDCA Cycle Essential for Establishment and Operation of ISMS and PMS
M@gicPolicyCoSMO is equipped with functions that allow ISMS and PMS activities to be carried out in line with the PDCA cycle. By working through the menu step by step, users can perform activities that meet the requirements of the relevant standards.
By using M@gicPolicyCoSMO to operate various ISMS and PMS activities, organizational activities and outcomes are centrally consolidated into the database, eliminating the need to rush to collect data and results just before audits.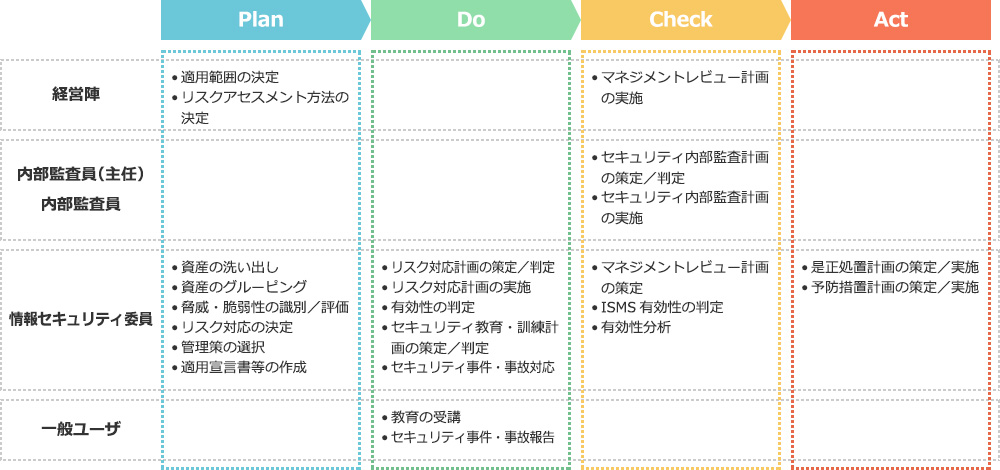
-
Standardized and Efficient Risk Assessment
In the ISMS version, during risk assessment work, a “threat and vulnerability table” related to each asset is listed, allowing users to identify and evaluate risks based on the risks provided by the tool. In addition, appropriate recommended controls are automatically selected based on the identified threats and vulnerabilities, enabling effective and comprehensive selection of security controls.
In the PMS version, there is a powerful function for risk identification and risk analysis: templates for risk identification are provided for each phase of the personal information handling lifecycle, from acquisition to disposal/erasure. This enables efficient execution of risk analysis, while also incorporating functionality to manage and track plans for addressing residual risks.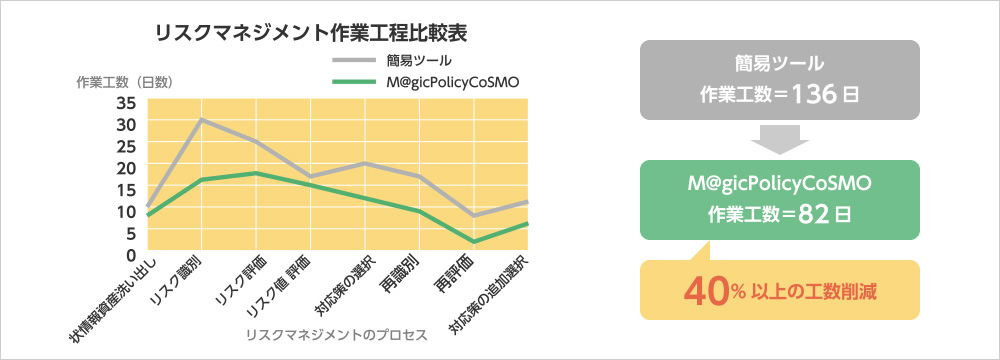
-
Security Education and Training to Support Continuous Improvement of ISMS and PMS
M@gicPolicyCoSMO automatically sends To-Do lists and emails notification to participants, prompting trainees to complete training sessions and tests in accordance with the training plan and schedule created by the training manager. Based on the trainees’ responses, the training manager can monitor participants’ response in real time and assess the organization’s level of awareness regarding information security and personal information protection. In addition, the system supports the periodic execution of tests and enables retesting for participants who do not achieve a passing score, thereby facilitating continuous improvement of ISMS and PMS through structured education and training. -
Internal Audit Execution
In the ISMS version, M@gicPolicyCoSMO automatically identifies the controls that have been implemented and presents audit items related to those controls. These audit items are aligned with ISO/IEC 27002 and JIS Q 27002. Internal auditors can use the presented audit items, as well as their own custom defined items, to share and divide internal audit work among multiple internal auditors. In addition to, based on the internal audit plan created by the chief internal auditor, the audit tasks assigned to each internal auditor can be distributed as To-Do lists, prompting them to carry out the internal audits.
In the PMS version, standard internal audit items are implemented in accordance with JIS Q 15001 and the “2nd edition of the Guidelines for Implementing a Personal Information Protection Management System based on JIS Q 15001:2006” (published by JIPDEC). Internal audits and inspections can be conducted by selecting items according to the audit objectives. As with the ISMS version, the presented audit items and user-defined audit items can be used to divide internal audit tasks among multiple internal auditors.
Deployment Patterns
Deployment Pattern 1: [Non-life Insurance] Sony Assurance Inc.
- Challenges:
-
Insufficient manpower within the ISMS administrative office
Need to reduce the operational burden on business units involved in ISMS activities
Requirement to conduct risk assessment for large volumme of information assets in a standardized and efficient manner
- Benefits:
- With the introduction of M@gicPolicyCoSMO, the organization was able to carry out the tasks required for ISMS establishment across the company in a consistent and efficient way.

Background of Focusing on the Information Security Management System (ISMS)
As a direct insurance company, we handle a large volume of customer information.
Since our establishment, we have believed that “for the company to survive and grow, we must earn the trust of our customers.” Even if business performance is strong, a single information leakage incident could undermine our social credibility and trust, leading to a crisis in business continuity and even the company’s survival. Our business model is “direct,” meaning that we interact directly with customers via telephone and the Internet. Therefore, security in communication is truly the core of our business continuity. To earn customer trust, we decided that it was crucial to thoroughly improve information security and to firmly implement ISMS activities as a key initiative.
In promoting “information security,” we had already implemented measures such as access control systems using ID card authentication and surveillance cameras as part of our internal infrastructure. However, rather than relying solely on isolated measures, we decided to construct an information security management system and pursue certification as one of our goals, in order to establish a more effective management cycle and embed information security across our organization.
In 2005, we were able to obtain certification (certification standard: BS 7799) ahead of the industry, with “head office-related divisions (planning and administration divisions)” and the “systems division” as the initial scope. However, as mentioned above, our most important information asset is “customer information,” which is handled extensively in frontline departments such as the Customer Center (call center), which receives policy applications, and the Service Center, which responds when accidents occur. Therefore, we decided to further expand our efforts to extend the scope of application to the entire company. As a result, in 2007 we achieved an industry-first certification with the entire company as the scope (certification standard: ISO/IEC 27001).
These initiatives both demonstrated our commitment to protecting valuable customer information and providing customers to feel secure in purchasing insurance from us and greatly contributed to raising security awareness among each and every employee.
Challenges in Establishing the ISMS
In promoting ISMS initiatives, our primary challenge was the limited availability of manpower , as a company still in a growth phase,. The administrative office was run by three people who were not dedicated full-time to ISMS but also had their primary duties. It was a primary challenge to achieve efficient operations that minimized the “sense of burden” on frontline staff so that ISMS activities would not interfere with their regular work.
In addition, our organization operates across major cities throughout Japan, making it difficult to uniformly share know-how on risk assessment across locations and other ISMS practices. Furthermore, the presence of large number of dispatched staff and subcontractor personnel added complexity to maintaining consist of information security controls, posing an additional challenge in ensuring effective governance.
Benefits and Advantages of Implementing M@gicPolicyCoSMO
To ensure thorough promotion of ISMS and strengthen the administrative function, we introduced M@gicPolicyCoSMO in combination with hands-on, operationally focused consulting services. With the introduction of M@gicPolicyCoSMO, the complexity of risk assessment work was reduced, and it became possible to manage information assets and conduct risk assessments in a standardized manner across all offices nationwide. In particular, the ability to easily assign risk levels to internal information assets and centrally manage them via the web was a very strong point.
Each department appointed an “ISMS representative ” responsible for risk assessment in that department. Because M@gicPolicyCoSMO’s operations are structured as workflows in accordance with the certification standards, even representative who did not yet have a deep understanding of ISMS were able to carry out their tasks smoothly and efficiently.
Furthermore, through the consulting engagement , our security vulnerabilities were thoroughly identified and clear, actionable recommendations were provided. This helpedclarify issues and developed more effective and practical risk treatment plans.
Even with a small administrative office, we were able to carry out all the work required for ISMS establishment simultaneously and efficiently across the entire organization. We strongly believe that the smooth, company-wide acquisition of ISO certification would not have been possible without the combined implementation of M@gicPolicyCoSMO and the professional consulting support.
Deployment Pattern 2: [Telecommunications Carrier] NTTPC Communications, Inc.
- Challenges:
-
The extensive workload associated with risk assessments and elated tasks was hindering the execution of the annual ISMS activity plan
Each change in risk mitigation or risk diversification approaches required risk assessment activities to be restarted from scratch
Additional effort was required to allocate and manage tasks in alignment with functional role separation and division of responsibilities.
- Benefits:
- By introducing M@gicPolicyCoSMO, the workload associated with risk assessment activities was significantly reduced, enabling the organization to maintain ISMS activities in line with expectations.

Background of Focusing on the Information Security Management System (ISMS)
At NTTPC Communications, we position security as the most important aspect of our business operation and have actively pursued the highest level of security practices. Our services provide span a wide range of business domains, including network services that build optimal network environments on the basis of large-scale infrastructure and highly reliable systems; on-demand services that combine services, technologies, and products to deliver the best solutions quickly; and corporate billing consolidation services that streamline customers’ accounting operations, as well as related network construction, maintenance, and system development.We have always made our best efforts to ensure a high level of information security for all of these solutions. As part of our Corporate Social Responsibility (CSR), we sought to demonstrate even more clearly to our stakeholders our firm commitment to security and obtained ISMS certification in February 2005 (certification registration number: IS 89520 / JIS Q 27001:2006 (ISO/IEC 27001:2005)).
Initially, the scope of certification was limited to certain parts of the organization, but during the 2007 surveillance audit we expanded it to cover the entire company. Based on CSR, we are continuing “spiral-up” activities aimed at achieving higher levels of information security.
Challenges in Establishing the ISMS
Three years after obtaining ISMS certification in 2005, we came to recognize that continuing the PDCA management cycle was even more meaningful than obtaining certification itself.
However, in the course of maintaining and continuing ISMS, one challenge was the large amount of work required for the periodic risk assessment, which is part of the PDCA management cycle.
Risk assessment activities demand both specialized knowledge and significant operational effort. From the perspective of knowledge, every time we changed the risk analysis method, we had to start over from explaining the method, and the work essentially returned to square one.
From the perspective of effort, risk assessment work was being carried out in each department using paper and spreadsheet software, which required a significant amount of work. Furthermore, because our organizational division of duties is complex, coordination among departments was also a source of difficulty.
While risk assessment is undoubtedly a critical activity. it is equally important to clarify define, manage and operate a wide range of ISMS activities such as internal audits and education and training. We therefore strongly believe that reducing the operational burden would enable us to realize more effective, reliable and expectation-aligned activities.
Benefits and Advantages of Implementing M@gicPolicyCoSMO
- Effective and efficient execution of risk assessments
- Progress management of plans and risk treatment measure
Following the surveillance audit conducted in 2007, we began considering the introduction of tools to build and operate ISMS. Many ISMS-related tools on the market focus on document management, but M@gicPolicyCoSMO offered functions to comprehensively support ISMS activities, including risk assessment and various ISMS tasks, based on the PDCA cycle. We therefore conducted that was the most suitable tool for the holistic management of the ISMS we had already established and decided to proceed with its implementation.
Because M@gicPolicyCoSMO allows ISMS operations to be carried out via the internal portal site, in risk assessment we were able to centrally manage information assets on the web, making it possible to efficiently identify information assets. In particular, we were able to reduce the workload associated with the most time-consuming tasks such as identifying information assets, evaluating and grouping asset values, and identifying and evaluating threats and vulnerabilities.
M@gicPolicyCoSMO incorporates the processes for risk assessment and the methods required for the work in a way that satisfies ISO/IEC 27001 requirements, so we believe we were able to appropriately conduct standardized risk assessments. Furthermore, with regard to the reproducibility of risk assessments required by the standard, we feel we were able to minimize variation.
During the process, we were able to check the results of risk assessment in various forms of reports, allowing us to quickly decide on risk acceptance criteria and levels, and to select effective controls and develop efficient risk treatment plans based on the results of risk assessment.
Regarding interdepartmental coordination and progress management of various plans, when tasks are requested from each department, it is essential to continuously monitor in each department’s status and provide timely support to those falling bhind when tasks are delegated. M@gicPolicyCoSMO provides functions that support various ISMS plans implemented under ISMS activities within the intranet environment. By fully utilizing these capabilities, we were able to centrally manage schedules and clearly assign responsibility for each plan. The system enables easy monitoring of task execution across departments, identification of delayed departments, and appropriate follow-up actions, resulting in smoother and more efficient operations, In external requests required significant time to compile and edit documentation. Now, by utilizing data stored in M@gicPolicyCoSMO, we cann present information directly or process it as needed, significantly reducing operational workload.
In conclusion, at NTTPC Communications we highly value the fact that introducing M@gicPolicyCoSMO has allowed us to maximize its benefits, improve the efficiency of ISMS activities, and focus more on the original purpose of ISMS activities—namely, the spiral-up of the PDCA management cycle.
«Internal materials used by the company to promote ISMS activities»
- “Laptop management” stickers
- “Clear desk, clear screen” stickers
- “Security patrol” armbands
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
