 An autonomous security product to protect connected vehicles and IoT devices from cyberattacks
XGuard Integrity (formerly Carwall)
An autonomous security product to protect connected vehicles and IoT devices from cyberattacks
XGuard Integrity (formerly Carwall)
 “Karamba XGuard CFI” received the Best of Show Award – Jury Special Prize (Security Category) at Interop Tokyo 2019.
Karamba XGuard CFI customized the CFI functionality—a core feature of XGuard Integrity—for IoT operating systems. Unlike conventional CFI products that validate only function calls, it also verifies the integrity of function returns (return addresses), providing robust protection against in memory attacks.
“Karamba XGuard CFI” received the Best of Show Award – Jury Special Prize (Security Category) at Interop Tokyo 2019.
Karamba XGuard CFI customized the CFI functionality—a core feature of XGuard Integrity—for IoT operating systems. Unlike conventional CFI products that validate only function calls, it also verifies the integrity of function returns (return addresses), providing robust protection against in memory attacks.
In recent years, the number of devices connected to the internet has continued to grow.
One area attracting particular attention is “connected cars,” which communicate with external services over the internet. While this brings greater convenience, it has also sparked frequent debate about safety and security.
For conversational IT systems, one of the most critical security risks is information leakage.
For connected cars—a representative type of IoT device—the greatest security risk requirements for such systems are fundamentally different from those of traditional IT environments and are subject to far more stringent and rigorous standards.
XGuard Integrity from Karamba Security is an autonomous security solution that hardens the software runtime environment of electronic control units (ECUs) and detects and blocks all attempted attacks.
Rather than fixing security bugs in code, XGuard Integrity prevents attacks that exploit such bugs by allowing only predefined, legitimate software behavior established during the manufacturing process of IoT devices.
・ Verifies runtime control flows in memory and protects against in-memory attacks.
・Enforces execution integrity by validating program behavior against.
・Controls internet connectivity of ECUs to avoid architectural weaknesses.
・Regulate external device inputs to prevent malware infections originating from peripheral devices.
Features of XGuard Integrity
-
Protection Against In-Memory Attacks
When automatically generating security policies for control units based on manufacturing-time settings, XGuard Integrity builds a call graph that maps the relationships between all function calls.
At runtime, the executing binary is inspected against this call graph to verify that the actual call sequence does not deviate from the expected behaviour defined at manufacturing time.
Because any in-memory attack used by an attacker to abuse a process will inevitably cause the process to diverge from the expected call graph, XGuard Integrity can detect and stop such attacks.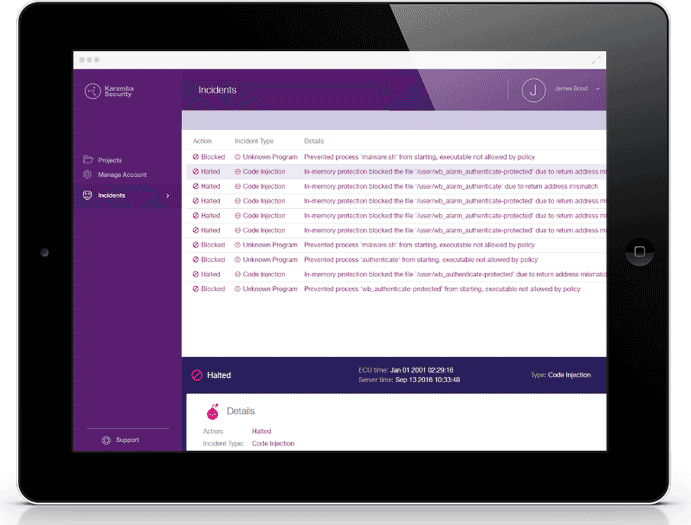
-
Allowing Only Predefined Code to Run
XGuard Integrity automatically generates a whitelist of allowed programs and scripts and prevents execution of any application not included in that list. Even if an attacker drops malware into flash storage, when the malware attempts to execute it will be recognized as a function does not present in the whitelist and will be blocked.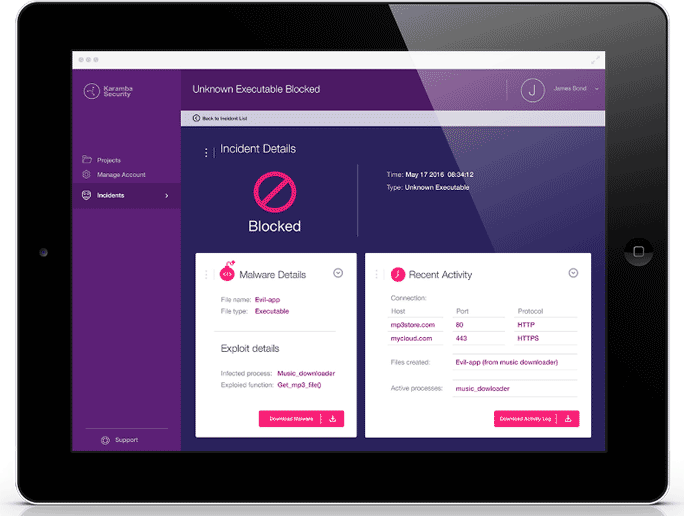
-
Automatic Policy Generation
During the generation of image files for ECU code, XGuard Integrity is automatically integrated into the ECU’s OS and then operates autonomously.
The Management Console provides visibility into the automatically generated policies, while while also offering the flexibility to customize these policies as required.
-
Runtime Protection and Incident Reporting
XGuard Integrity continuously monitors all code execution and decides in real time whether to allow or block code at runtime.
If an attacker attempts to run external code or launches in-memory attacks against various functions, the product detects and blocks these actions, and generates a report containing detailed contextual information about the attack.
This provides both protection and forensic data to help identify vulnerabilities, enabling rapid response and remediation. -
Minimal Performance Impact
XGuard Integrity is designed with optimal performance in mind.
Even while enforcing security policies, it uses only about 1–2% of CPU resources.
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
