Connected Car
Security
Protecting Vehicles from Internet-Based Threats to Enable Safer and More Convenient Mobility
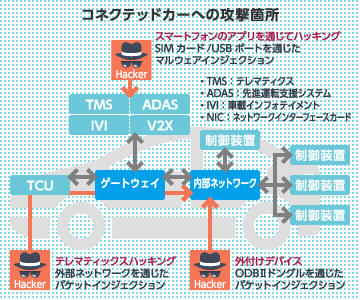
Connected cars, - vehicles that are connected to the internet and enable ADAS (Advanced Driver Assistance Systems) and autonomous driving, are drawing increasing attention. By transmitting and collecting information via the internet and applying advanced analytics , these vehicles can provide real-time road conditions, help understand and mitigate traffic congestion, and are expected to be used for accident reporting and insurance applications. At the same time, however, increased Internet connectivity gives rise to growing security concerns, highlighting the importance of robust cybersecurity measures. .
Asgent’s connected car security solutions provide the essential security required for a connected car society by protecting, not only for the connected vehicles themselves, but also for the surrounding ecosystem in which they operate.
- Establishment of a Robust Security Framework.
- ECU Security
- Authentication for In-Vehicle Networks
- Hardening of Mobile Applications
- Vehicle SOC Solutions
Taking a New Approach to Address Emerging Security Risks

File Sanitization
Measures
Countermeasures Against File-Based Cyber Threats Delivered by an Industry Leaders in Threat Sanitization
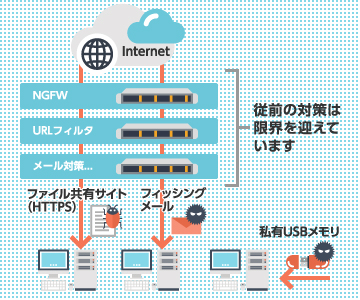
In recent years, targeted attacks have been increasing, exposing many organizations to a higher risk of being targeted. At the same time, attack vectors have become increasingly sophisticated , shifting from conventional direct attacks by hackers to methods that leverage social engineering, such as phishing emails, file downloads from the web, and even visits to malicious websites.
The security market has grown enormous, and there is now a vast array of countermeasures. However, even with the implementation of multi-layered security controls, many organizations have been unable to fully prevent infections by viruses, malware and ransomeware. One of the key reason conventional security measures have proven insufficient is that many of them rely on signature-based detection and pattern matching, rendering them inefffective against zero-day attacks and sophisticatd attacks.
As a new approach to cybersecurity, Asgent proposes file sanitization as an effective countermeasure.
- File sanitization
This technology disassembles files entering an organization through email, file-sharing services, USB memory devices, and other channels, removes and neutralizes malicious code, and then reconstructs the file in the sale form.
Preparing for Today’s Most Critical Threat: Targeted Cyberattacks

Targeted Attack Countermeasures
Preparing for Sophisticated Targeted Attacks That Demand Comprehensive Security Measures
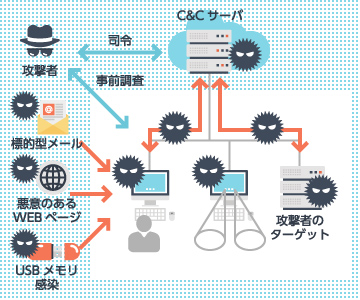
Targeted attacks are cyberattacks aimed at specific companies or organizations. Their goal is not limited to stealing highly valuable financial or confidential information. As seen in attacks associated with groups such as Anonymous, many attacks also target organizations whose values, beliefs, or perceived “justice” conflict with those of the attackers.
Targeted attacks are cyberattacks aimed at specific companies or organizations. Their goal is not limited to stealing highly valuable financial or confidential information. As seen in attacks associated with groups such as Anonymous, many attacks also target organizations whose values, beliefs, or perceived “justice” conflict with those of the attackers.In practice, the attack methods are highly diverse and extremely persistent, with attackes employing a wide range of techniques until their objectives are achieved. Representative methods include “spear-phishing emails” that abuse social engineering and “watering hole attacks,” where users are lured into viewing a website that delivers malicious programs.
Because these sophisticated attacks continue in many different forms until the attackers succeed, it is impossible to completely block all of them at the perimeter using only firewalls, IPS, and other gateway defenses. Accordingly, organizations must implement multiple layered security measures beyond traditional perimeter controls.
Asgent proposes multilayered defenses that combine multiple products and services, including blocking suspicious communications at the perimeter, countermeasures against unknown threats, and support for building CSIRT (Computer Security Incident Response Team) capabilities.
Asgent proposes an optimal framework for countering targeted attacks.
- Detect early signs of attacks to prevent or minimize damage
- Implement countermeasures against unknown threats
Strengthening Security at Each Key Point Exposed to Threats

Web
Security
Enhancing Web Security to Counter Diverse and Evolving Attack Vectors
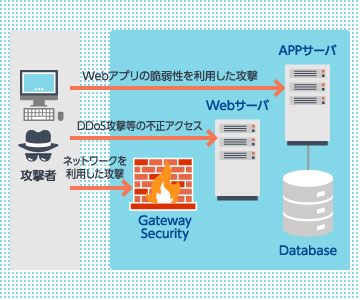
Websites operated by customers as well as web applications developed using the similar technologies, are constantly exposed to various external threats. Typical examples include attacks that exploit vulnerabilities to break into internal systems and cause information leaks or website defacement, and denial-of-service (DoS) attacks that forcibly disrupt business operations from the outside. By their very nature, websites and web applications require continuous security measures.
If such attacks result in website defacement or information leakage, the consequences—such as damage to your brand, loss of trust, or incuurrence of liability and compensation claims —are clearly unacceptable and cannot be taken lightly..
Asgent’s web security solutions cover a wide range of needs, including assessments to verify whether customers’ websites are adequately protected against external threats, performing vulnerability assessments of servers, software, and web applications, and providing services that protect live websites from DoS attacks.
Asgent proposes an optimal framework for web security.
- Protect websites from cyberattacks
- Identify and assess vulnerabilities in websites

Email
Security
Strengthening the Security of Mission-Critical Email Communications
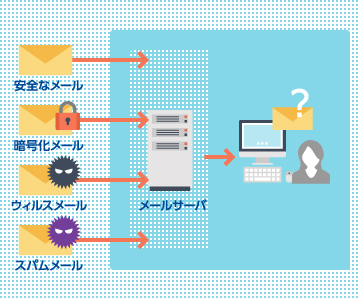
Email has become a widely adopted and mission-critical infrastructure. It is frequently used to exchange highly sensitive information, the email addresses themselves constitute personal data, and the email is one of the tools most commonly abused by attackers to distribute malware and other threats. Thes include attachment encryption and misdelivery prevention, as well as effective measures to ensure the safe receipt of email attachments.
Asgent’s email security solutions enable secure email sending and receiving without sacrificing usability, while also ensuring that attachments can be received safely.
Asgent proposes optimal mechanisms for email security tailored to your environment.
- Sanitize attachments
- Send attachments safely

Mobile
Security
Enabling Secure Use of Mobile Devices While Protecting Against Security Threats
Smartphones and tablets now offer capabilities comparable to desktop PCs, and with the growing use of email and cloud-based file sharing, their use in business is expanding rapidly. At the same time, security risks such as credential theft through phishing sites and the download of malicious applications are also increasing. For this reason, mobile devices now require the same comprehensive security measures as desktop PCs. Asgent’s mobile security solutions help ensure the safe business use of mobile devices by blocking access to phishing sites, detecting malware, and providing protection equivalent to that of desktop PCs.
Asgent proposes optimal mechanisms for mobile security tailored to your environment.
- Strengthen mobile security to the same level as internal PCs
- Prevent malware infection on mo

Cloud
Security
Ensure Security in Public Cloud Environments
As the phrase “cloud first” suggests, many corporate IT organizations are actively migrating, or considering migrating, a growing volume of information assets to the cloud. However, even in cloud services, it is essential to understand the shared responsibility model and implement appropriate security measures. In particular, for IaaS in public cloud environments, responsibility for the OS running on the hardware, databases, applications, and account management lies with the customer organization.
Asgent’s cloud security solutions protect your assets from the latest attacks while providing visibility into your security configurations.
Asgent’s cloud security solutions protect your assets from the latest attacks while providing visibility into your security configurations.
- Protect against the latest cyber threats
- Gain visibility into potential security misconfigurations
- Strengthen the organization’s information security management framework
Assess the Current State of Security Posture, from Control Strength to the Presence of Vulnerabilities

Security
Assessment
Gaining Visibility into the Current Security Posture of the Websites and Internal Networks
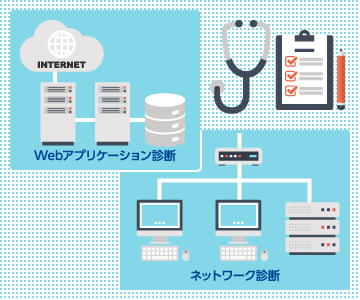
To identify potential vulnerabilities, two types of assessments are offered: Platform Assessments and Web Application Assessments. A Platform Assessment evaluates servers, network devices, operating systems, and middleware to identify vulnerabilities and configuration issues. A Web Application Assessment focuses on whether there are vulnerabilities or configuration flaws in web applications. Assessment methods include automated testing with tools and manual testing by consultant security engineers. Manual testing can reveal vulnerabilities and behaviors that are difficult to detect with tools alone.
In addition, Penetration Testing, also known as an intrusion test, is used to verify whether an attacker could actually achieve their objectives through simulated attacks and to evaluate the effectiveness of your current security measures. In penetration testing, attack scenarios that real attackers are likely to use are designed and executed. The assessment looks not only at whether vulnerabilities exist, but also at attacker behavior after intrusion and whether high-risk information assets could be exposed, providing a view from the attacker’s perspective.
Asgent provides system vulnerability assessments as well as penetration testing.
Asgent proposes optimal mechanisms for security assessment.
- Identify whether vulnerabilities exist
- Assesses the effectiveness of your current security measures

Risk
Management
Build an Internal Security Framework that Delivers Strong Security and Addresses Diverse Risks / Obtain Certifications
As security incidents continue to spread, many organizations are required to establish robust internal security frameworks. At the same time, organizations are increasingly required to obtain various certifications to maintain and enhance their credibility in the market. By using information security audits and other mechanisms, and by adopting support from professional consultants together with the right tools, companies can implement risk management more smoothly and effectively.
Asgent provides comprehensive support for establishing internal security frameworks, as well as consulting services to assist with the acquisition of various certifications, including ISMS.
Asgent proposes optimal mechanisms for risk management.
- Obtain security certifications
- Undergo security audits
- Strengthen the organization’s internal security framework
Enhancing the Resilience of Local Government Information Systems

Local
Government Security
Implement File Sanitization and Advanced Countermeasures against Unknown Malware Required under the “Local Government Information System Resilience Enhancement Model”
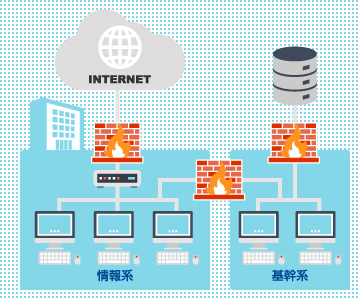
Information-leak incidents caused by malware embedded in email attachments – used to steal confidential data from enterprises and public organizations – continue unabated. In response, the Ministry of Internal Affairs and Communications’ Local Government Information Security Measures Study Team, made up of outside experts, released a report in November titled “Toward Fundamental Reinforcement of Local Government Information Security Measures.” The report recommends strengthening the monitoring of unauthorized communications through a “Local Government Information Security Cloud,” separating business systems connected to LGWAN (the Local Government Wide Area Network used for My Number–based information linkage) from systems connected to the internet, and ensuring “sanitized” communication so that no malware can be carried between the two.
In addition to file sanitization products and solutions for detecting infections by unknown malware, Asgent also offers managed security services that provide external monitoring for security products, delivering security solutions optimized for local governments.
Asgent provides optimal mechanisms for local government security.
- Sanitize and neutralize threats embedded in email communications
- Detect the intrusions of unknown and zero-day malware
- Strengthen continuous monitoring capabilities against malware infections
Addressing Today’s Critical Security Challenges

Supply Chain
Security
Preparing for Cyberattacks Originating from Business Partners and Third-Party Services
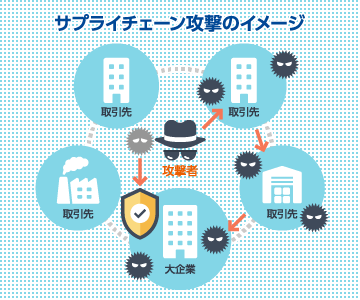
“Supply Chain Attacks” refer to cyberattacks that target a primary organization by first compromising its suppliers, partners, or service providers are known as supply chain attacks. In recent years, this has emerged as a significant threat, consistently ranked among the top positions in “Top 10 Information Security Threats” published annually by IPA (Information-technology Promotion Agency, Japan).
To address the critical risks associated with Supply Chain Attacks, Asgent provides comprehensive assessment and diagnostic services designed to visualize and evaluate an organization’s current security posture.
Asgent proposes optimal mechanisms for supply chain attack countermeasures.
- Attack Surface Management (ASM)
- Vulnerability Assessment Services

Zero Trust
Strengthening Resilience against Evolving Security Threats Originating from both Internal and Exernal Emvironments
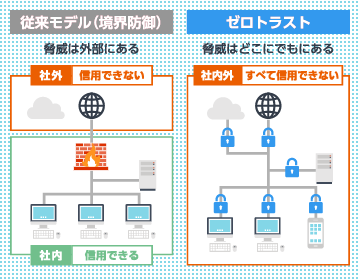
Traditional security models were based on the assumption that the information assets to be protected stayed inside the corporate network and that threats came from outside. Based on this assumption, security measures were implemented at the boundary between the internal and external networks, a concept known as perimeter defense.
However, with the increased use of cloud services and the and the diversification of work environments, such as remote work, the location of devices and the data they access are no longer limited to the office walls. As a result, the “perimeter” itself has become blurred, and perimeter-based measures alone are no longer sufficient.
This is why the “Zero Trust2 concept is attracting attention. In the Zero Trust model, security threats are assumed to exist not only outside the corporate network but also inside it, and nothing that attempts to access internal resources is trusted by default. Every access request must be verified.
Asgent provides solutions that inspect all communications and make it possible to realize zero trust.
Asggent offers optimal mechanisms for zero trust security, including:
- SASE
- Endpoint security (EDR/EPP)
- File sanitization solutions