 CTER solution patches vulnerabioities even before vendor fixes are available
Vicarius VRX
CTER solution patches vulnerabioities even before vendor fixes are available
Vicarius VRX
Interop 2025 – Best of Show Award
Security (Enterprise) Category – Runner-Up
Simply identifying vulnerabilities is insufficient for effective defense. Vicarius vRx transforms your security posture by analyzing the enormous volume of vulnerability data to pinpoint the threats that are truly paramount to your organization. It instantly identifies and prioritizes the most critical risks, enabling immediate defensive action. Vicarius vRx accelerates the deployment of vendor patches and offers flexible mitigation for unpatched risks through scripting and virtual patching. This is a critical shift: moving beyond mere Vulnerability Management to comprehensive Exposure Management.
Stop struggling with vulnerability management and patching
The Growing Risk of Cyberattacks and the Criticality of Vulnerability Management
The volume of security incidents continue to increase year by year, and many unauthorized access attacks target system vulnerabilities.
However, with more than 100 new vulnerabilities disclosed every day, it is simply not realistic to fix them all. That’s why risk-based prioritization and rapid remediation are essential.
If Defense Is Delayed, Risk Will Escalate Exponentially
Attackers initiate campaigns targeting newly disclosed vulnerabilities immediately – often within mere days of public announcement. A delayed response directly translates to service risks, including service disruption and deep organizational compromise.
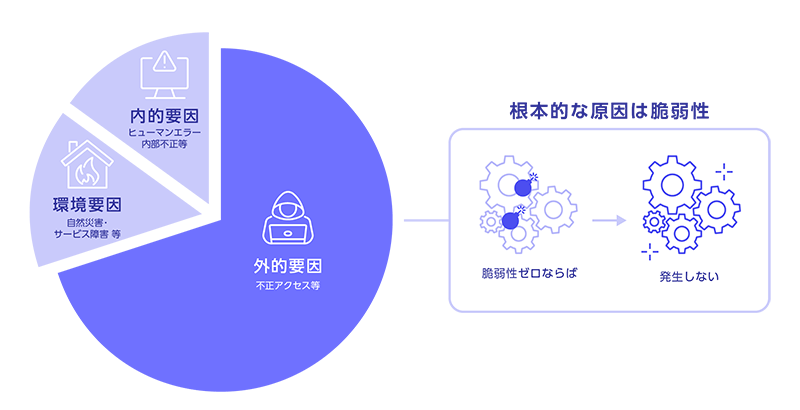
Four Critical Challenges We Face Now
Amidst the vast influx of vulnerability intelligence, security teams struggle with the difficulty of risk-based prioritization, the complexity of management patches for applications beyond the OS, the critical exposure gap before official vendor fixes are released, and the operational overhead associated with disparate, multi-tool security environments.
Inability to identify truly critical risks
Complexity of non-OS application patch management
The critical exposure gap before official patches arrive
Tool sprawl drives up cost and operational burden
Amidst the massive flood of vulnerability intelligence, organizations face difficulty in determing which items to prioritize for remediation, resulting in the persistence of potentially severe, unaddressed risks within the environment.
The lack of established patching procedures for non-OS applications, such as browsers and business software, leads to significant inconsistency in vulnerabilities across endpoints and systems, ultimately weakening the enterprise’s overall security posture.
The inherent delays in vendor patch releases, coupled with complete lack of patches for systems that have reached End-of Support (EOS), result in prolonged period of defenseless, significantly elevating the attach surface risk.
Because vulnerability scanning, risk assessment, and patch deployment are managed by separate and disconnected tools, organizations face escalating license costs and excessive operational overhead, necessitating on immediate re-evaluation of the security attack.
Vicarius vRx: Achieving Simple and Powerful Vulnerability Management and Patching
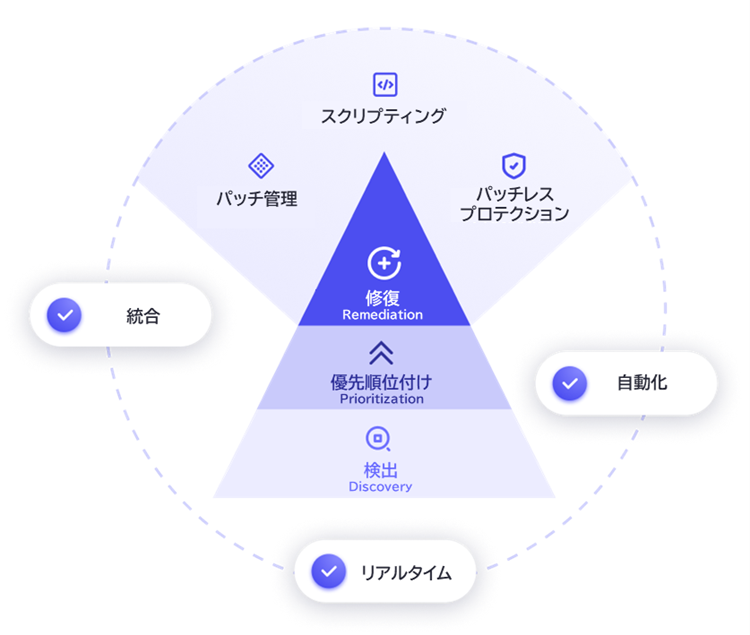
Vicarius vRx provides a one-stop solution to all these challenges through its three core pillars of capability: Analyze, Prioritize and Remediate.
Analyze: Accurately Grasping Your Vulnerability Landscape
The analyze function continuously identifies operating systems and applications in use, providing teal-time visibility into all assets and potential risks. It performs correlation analysis of CVSS scores, the Exploit Database, and system usage metrics to precisely identity the “truly exploitable vulnerabilities.”
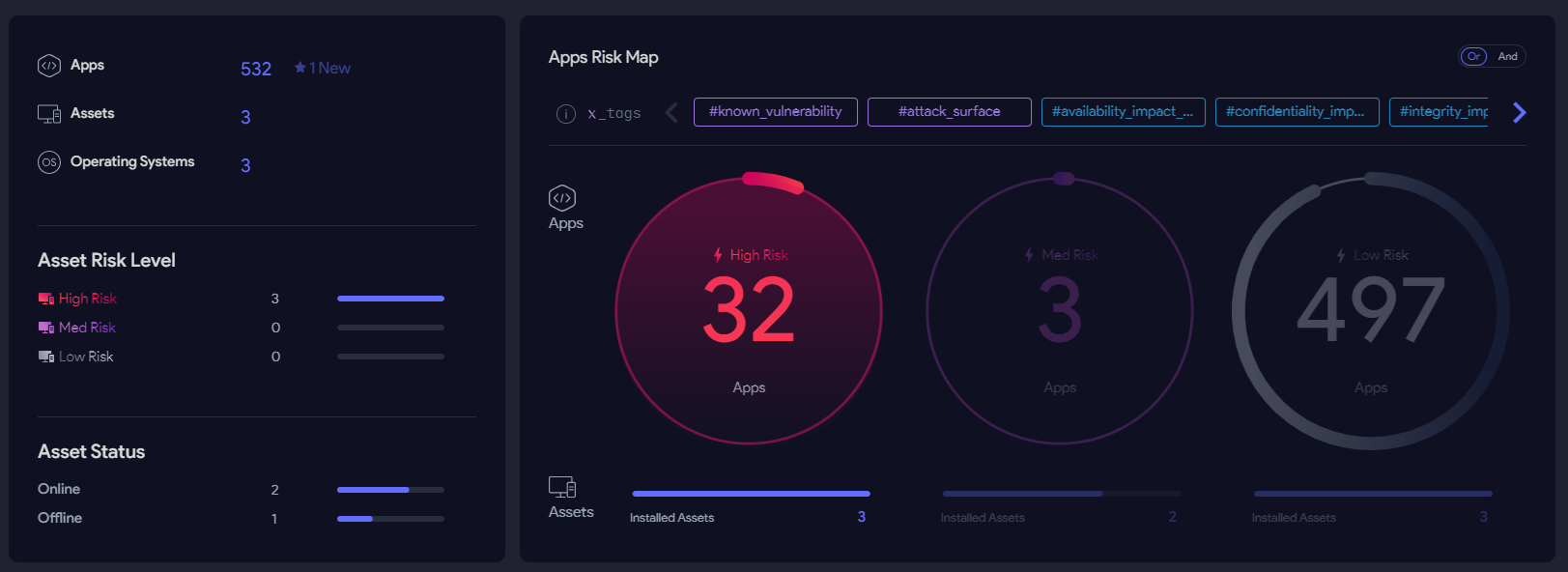
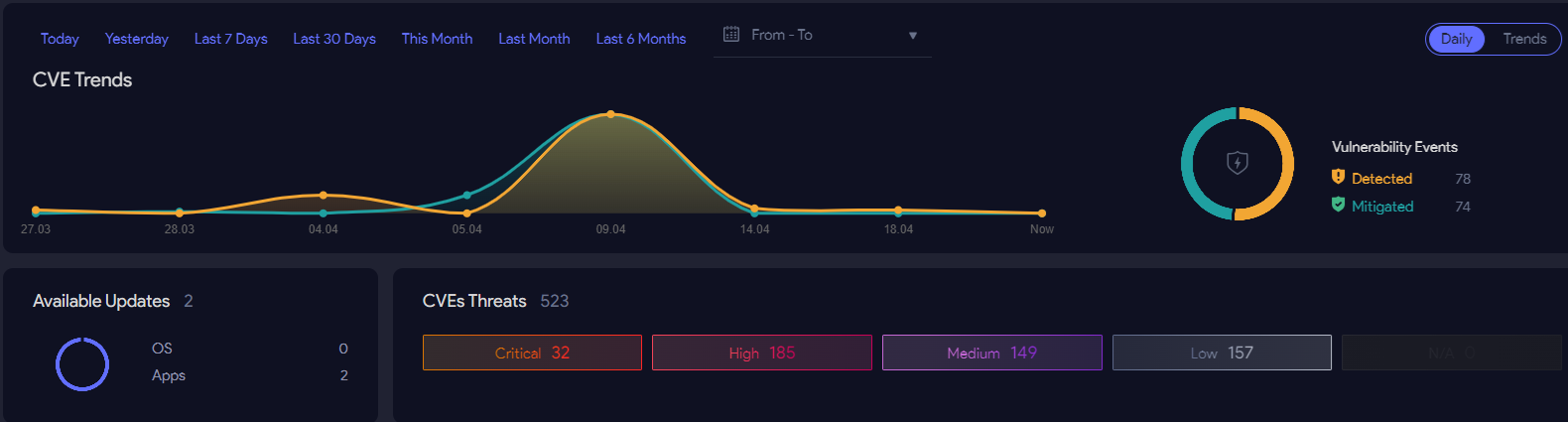
Prioritize : Instantly Identify the Most Critical Vulnerabilities
Uniformly addressing every vulnerability is simply not practical.
Vicarius vRx tackles this by scoring risk based on both exploitability and potential impact. This enables organizations to establish a framework for efficiently addressing vulnerabilities, starting with the highest-priority risks.
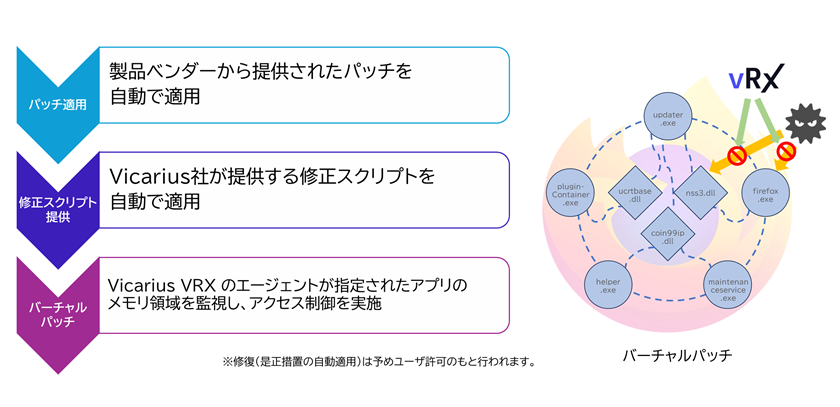
Remediate: Immediate Defense via Virtual Patching and Automated Mitigation
The Remediate function presents prioritized remediation actions for vulnerabilities, significantly reducing the cost and effort involved in security countermeasures. Even in cases where official patches are unavailable or when facing zero-day vulnerabilities, the vRx Agent provides instant defense using its proprietary “Virtual Patching” technology, which proactively protects vulnerable process. Furthermore, in environments where patch deployment is difficult, vRx automatically applies alternative mitigation measures, such as configuration changes, to prevent system compromise. This capability optimizes the time and resources spent on vulnerability management.
Evolve Beyond Vulnerability Visibility: Achieve Full Exposure Management with Vicarius vRx
Accurately Assess Risk, Rapidly Prioritize Action, and Instantly Defend Assets
This is the new standard of vulnerability management required today.
Vicarius vRx will lead your organization’s security operations to the next stage.
Simply identifying vulnerabilities is insufficient for effective defense. Vicarius vRx transforms your security posture by analyzing the enormous volume of vulnerability data to pinpoint the threats that are truly paramount to your organization. It instantly identifies and prioritizes the most critical risks, enabling immediate defensive action. Vicarius vRx accelerates the deployment of vendor patches and offers flexible mitigation for unpatched risks through scripting and virtual patching. This is a critical shift: moving beyond mere Vulnerability Management to comprehensive Exposure Management.
Stop struggling with vulnerability management and patching
The Growing Risk of Cyberattacks and the Criticality of Vulnerability Management
The volume of security incidents continue to increase year by year, and many unauthorized access attacks target system vulnerabilities.
However, with more than 100 new vulnerabilities disclosed every day, it is simply not realistic to fix them all. That’s why risk-based prioritization and rapid remediation are essential.
If Defense Is Delayed, Risk Will Escalate Exponentially
Attackers initiate campaigns targeting newly disclosed vulnerabilities immediately – often within mere days of public announcement. A delayed response directly translates to service risks, including service disruption and deep organizational compromise.

Four Critical Challenges We Face Now
Amidst the vast influx of vulnerability intelligence, security teams struggle with the difficulty of risk-based prioritization, the complexity of management patches for applications beyond the OS, the critical exposure gap before official vendor fixes are released, and the operational overhead associated with disparate, multi-tool security environments.
| Inability to identify truly critical risks | Complexity of non-OS application patch management | The critical exposure gap before official patches arrive | Tool sprawl drives up cost and operational burden |
|---|---|---|---|
| Amidst the massive flood of vulnerability intelligence, organizations face difficulty in determing which items to prioritize for remediation, resulting in the persistence of potentially severe, unaddressed risks within the environment. | The lack of established patching procedures for non-OS applications, such as browsers and business software, leads to significant inconsistency in vulnerabilities across endpoints and systems, ultimately weakening the enterprise’s overall security posture. | The inherent delays in vendor patch releases, coupled with complete lack of patches for systems that have reached End-of Support (EOS), result in prolonged period of defenseless, significantly elevating the attach surface risk. | Because vulnerability scanning, risk assessment, and patch deployment are managed by separate and disconnected tools, organizations face escalating license costs and excessive operational overhead, necessitating on immediate re-evaluation of the security attack. |
Vicarius vRx: Achieving Simple and Powerful Vulnerability Management and Patching
Vicarius vRx provides a one-stop solution to all these challenges through its three core pillars of capability: Analyze, Prioritize and Remediate.
Analyze: Accurately Grasping Your Vulnerability Landscape
The analyze function continuously identifies operating systems and applications in use, providing teal-time visibility into all assets and potential risks. It performs correlation analysis of CVSS scores, the Exploit Database, and system usage metrics to precisely identity the “truly exploitable vulnerabilities.”

Prioritize : Instantly Identify the Most Critical Vulnerabilities
Uniformly addressing every vulnerability is simply not practical. Vicarius vRx tackles this by scoring risk based on both exploitability and potential impact. This enables organizations to establish a framework for efficiently addressing vulnerabilities, starting with the highest-priority risks.

Remediate: Immediate Defense via Virtual Patching and Automated Mitigation
The Remediate function presents prioritized remediation actions for vulnerabilities, significantly reducing the cost and effort involved in security countermeasures. Even in cases where official patches are unavailable or when facing zero-day vulnerabilities, the vRx Agent provides instant defense using its proprietary “Virtual Patching” technology, which proactively protects vulnerable process. Furthermore, in environments where patch deployment is difficult, vRx automatically applies alternative mitigation measures, such as configuration changes, to prevent system compromise. This capability optimizes the time and resources spent on vulnerability management.

Evolve Beyond Vulnerability Visibility: Achieve Full Exposure Management with Vicarius vRx
Accurately Assess Risk, Rapidly Prioritize Action, and Instantly Defend Assets
This is the new standard of vulnerability management required today. Vicarius vRx will lead your organization’s security operations to the next stage.

Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
