 Early Detection Platform for ECU Vulnerabilities
ThreatHive
Early Detection Platform for ECU Vulnerabilities
ThreatHive
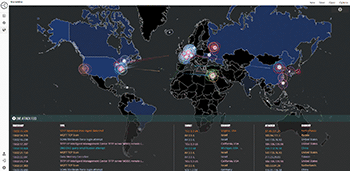 Karamba ThreatHive functions as a threat intelligence command center. By deploying honeypots worldwide, it identifies and tracks real-world cyberattacks. By deploying protected ECU software on these honeypots, you can accurately understand the actual attack surface.
Karamba ThreatHive functions as a threat intelligence command center. By deploying honeypots worldwide, it identifies and tracks real-world cyberattacks. By deploying protected ECU software on these honeypots, you can accurately understand the actual attack surface.
Main Functions and Features
-
Rapid Detection
Attackers continuously scan for vulnerable targets and launch attacks accordingly. ThreatHive records and analyzes attack activity and provides detailed threat forensics. By analyzing this forensic data, you can remediate ECU vulnerabilities and software defects. -
Collection of Actionable Data
ThreatHive operates a continuously running, global honeypot system to collect threat intelligence and identify security gaps. Dashboards and aggregated reports display details such as hacking attempts, threat types, target systems, and attack timelines. The availability of detailed data and guidance supports the evaluation of security countermeasures, while the collected data can be used with replay tools to reproduce observed incidents. -
Cost Reduction
Rather than relying solely on penetration testing during the quality assurance phase, ThreatHive offers a cost-effective way to complement and accelerate penetration testing during development. This continuous testing approach does not place additional burden on developers and does not impact time-to-market.
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
