Features of Check Point Virtual Systems
-
Reduced TCO through consolidated network security
In recent years, consolidating network security has attracted attention as a strategy to strengthen security while reducing costs.
With Check Point Virtual Systems, you can create up to 250 completely independent Virtual Systems. This significantly reduces hardware investment, rack space, and operational management costs, while improving manageability, scalability, availability, and performance. By consolidating network security, you not only reduce hardware investment but also streamline security operations for large-scale networks and data centers segmented into multiple zones, thereby lowering both capital and operational expenditures.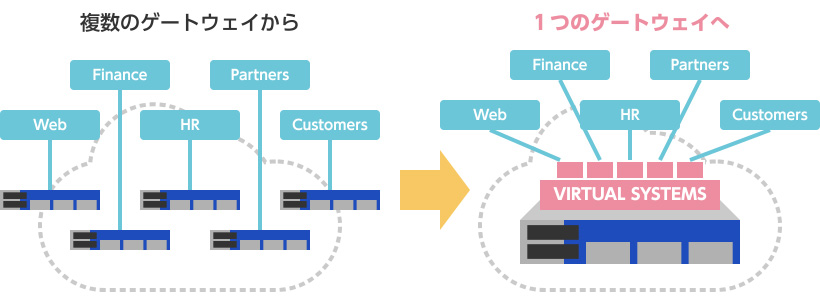
-
Flexible combination of Software Blades
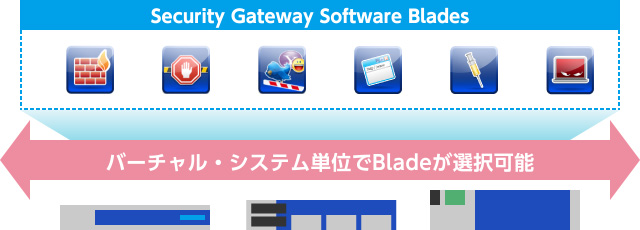
You can use Software Blades on a per–Virtual System basis. This allows you to customize security policies for each individual network or VLAN that makes up a complex network infrastructure, tailoring them to specific requirements. By minimizing policy complexity in this way, you can implement more effective security that aligns with business needs.
-
Per–Virtual System policy configuration and resource monitoring
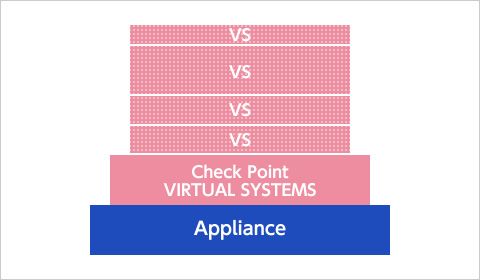 Because you can define network security policies for each Virtual System, it is possible to customize policies in line with business requirements.
Because you can define network security policies for each Virtual System, it is possible to customize policies in line with business requirements.
In addition to security policies, CPU and memory usage can be monitored in detail for each Virtual System, giving you clear visibility into resource utilization. By using the resource control function, you pre-assign only the memory and CPU resources necessary for each Virtual System’s tasks, allowing you to control its maximum processing capacity.
Resources no longer needed by one Virtual System are automatically made available to others.
You can also limit CPU resources for lower-priority Virtual Systems and allocate more capacity to mission-critical ones. -
Easy deployment and efficient centralized manage
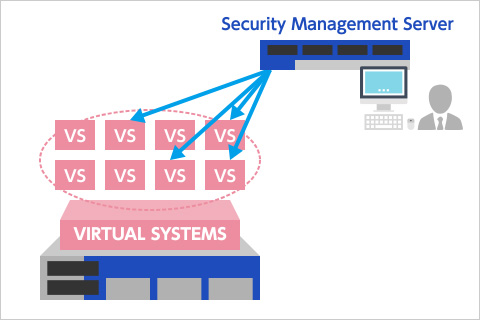
You can efficiently manage each Virtual System using Check Point Security Management Server and Multi-Domain Security Management Server. By preparing dedicated Virtual Systems for functions such as web security, threat prevention, firewall, and remote access, you can clearly separate administrative responsibilities and reduce operational workload.
In addition, by separating management data for each Virtual System, service providers can offer cloud-based SaaS services.
Product Lineup
Number of Virtual Systems
| Model | Maximum number of VSs (maximum memory) |
|---|---|
| 3600 | 5VS(8GB) |
| 3800 | 10VS(16GB) |
| 6200 | 20VS(32GB) |
| 6400 | 20VS(32GB) |
| 6600 | 20VS(32GB) |
| 6700 | 20VS(32GB) |
| 7000 | 20VS(64GB) |
| 16200 | 250VS(128GB) |
| 26000 | 250VS(128GB) |
| 28000 | 250VS(128GB) |
Deployment patterns
Deployment pattern 1: Consolidating multiple security gateways
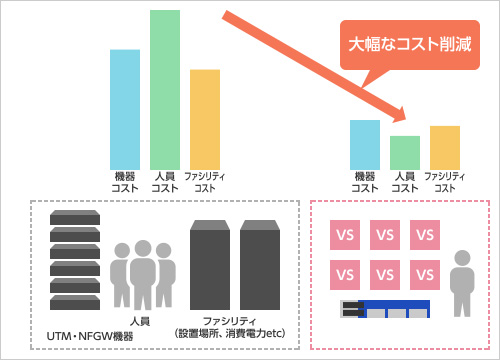 You can run multiple security functions on a per–Virtual System basis without compromising security.
You can run multiple security functions on a per–Virtual System basis without compromising security.
By consolidating everything onto a single hardware platform, you can significantly reduce costs through savings on rack space and thousands of watts of power consumption.
Fewer hardware units also ease the burden on administrators and help reduce personnel costs. You maintain industry-leading security capabilities while reducing power consumption, footprint, and overall costs.
Deployment pattern 2: Consolidating multiple security gateways in multi-tenant environments
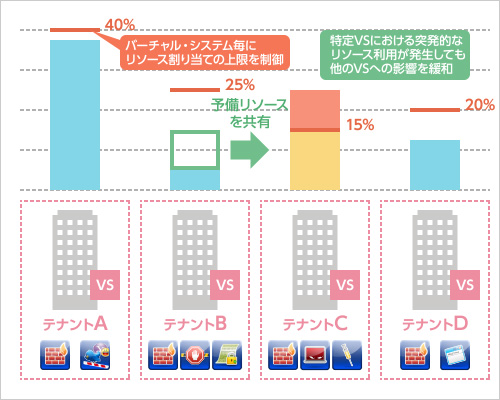 This product supports multi-tenancy, enabling a single system to handle different policy settings and resource monitoring for multiple customers or departments. You can not only assign different policies to each tenant, but also freely combine Software Blades to provide the optimal security environment tailored to each tenant’s specific requirements. The resource control function lets you distribute processing by allocating only the necessary CPU and memory resources to each Virtual System. As a result, even if one Virtual System’s resource usage spikes, you can prevent it from affecting other Virtual Systems.
This product supports multi-tenancy, enabling a single system to handle different policy settings and resource monitoring for multiple customers or departments. You can not only assign different policies to each tenant, but also freely combine Software Blades to provide the optimal security environment tailored to each tenant’s specific requirements. The resource control function lets you distribute processing by allocating only the necessary CPU and memory resources to each Virtual System. As a result, even if one Virtual System’s resource usage spikes, you can prevent it from affecting other Virtual Systems.
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
 Virtual security gateway that consolidates and simplifies security for private cloud environments
Virtual security gateway that consolidates and simplifies security for private cloud environments