Check Point uses security licenses known as Software Blades.
By using these Software Blades, you can introduce a wide range of security functions on open servers and in virtual environments. Even when your organization’s security requirements change and new countermeasures are needed, you can simply add new security licenses to expand functionality without changing the underlying hardware platform.
By using these Software Blades, you can introduce a wide range of security functions on open servers and in virtual environments. Even when your organization’s security requirements change and new countermeasures are needed, you can simply add new security licenses to expand functionality without changing the underlying hardware platform.
Features of Check Point Software Licenses
-
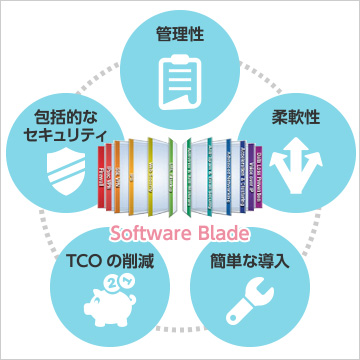
Manageability
Centralized management enables rapid deployment of security functions and helps improve productivity. -
Comprehensive security
Delivers the right level of security at every enforcement point and across all layers of the network. -
Flexibility
Allows you to obtain the appropriate level of security with the right level of investment. -
Reduced TCO
By consolidating multiple security functions on existing hardware, overall expenditure can be kept to a minimum.。 -
Easy deployment
Software Blades can be deployed on Check Point next-generation firewall appliances, open servers, virtual environments, and even endpoints.
Functions that you wish to add later can be enabled easily without adding new hardware, firmware, or drivers. This allows you to introduce security capabilities dynamically as needed, while keeping costs under control.
Software Blade architecture lineup
The Software Blade architecture offers a wide range of Software Blades that provide both security gateway functions and security management functions as modular components, and new capabilities are being added every year. Because Software Blades are modular and easy to migrate, you can add or customize gateway and management functions to match environment-specific requirements and their evolution—without needing to deploy new hardware.
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
 Industry-first security architecture with exceptional flexibility and scalability
Industry-first security architecture with exceptional flexibility and scalability