Powered by the same advanced security technologies used by Fortune 100 companies, Quantum Spark protects networks against sophisticated cybercrime and zero-day threats such as viruses, spam, and malicious websites. Despite its powerful capabilities and easy-to-use web-based management, it is priced to fit the limited budgets typically found in SMB environments.
Key features of Check Point Quantum Spark
-
Enterprise-class performance at an affordable price
Sophisticated threats often infiltrate and lie dormant in the network through multiple stages, making them difficult to detect. Quantum Spark combines industry-leading firewall technology with advanced IPS and detection engines to protect against these complex cyberattacks.
It delivers the enterprise-grade performance needed to address such threats, while also providing the responsiveness and flexibility that SMBs require—all in a cost-effective appliance.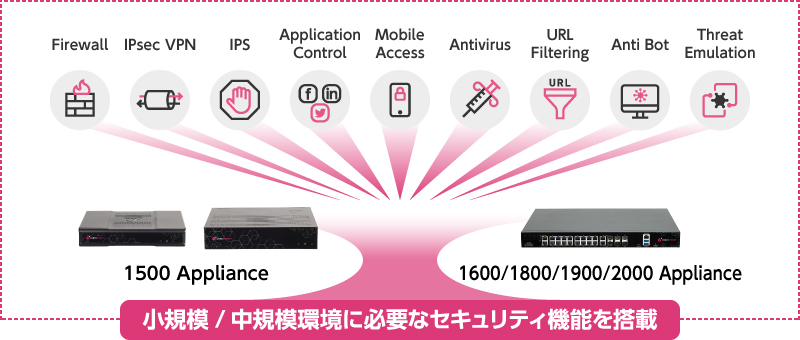
-
Easy deployment and simple management
Overly complex systems with too many confusing or unused features are difficult to operate. Quantum Spark uses a wizard-based initial setup interface, allowing you to complete a few simple steps and start operations in just a few minutes.
Monitoring and reporting are also straightforward, enabling smooth deployment even in branch or remote office environments that do not have dedicated IT staff.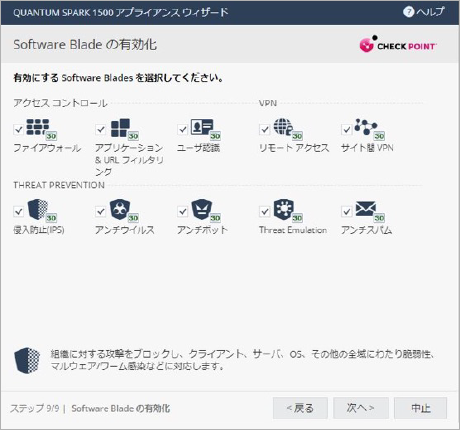
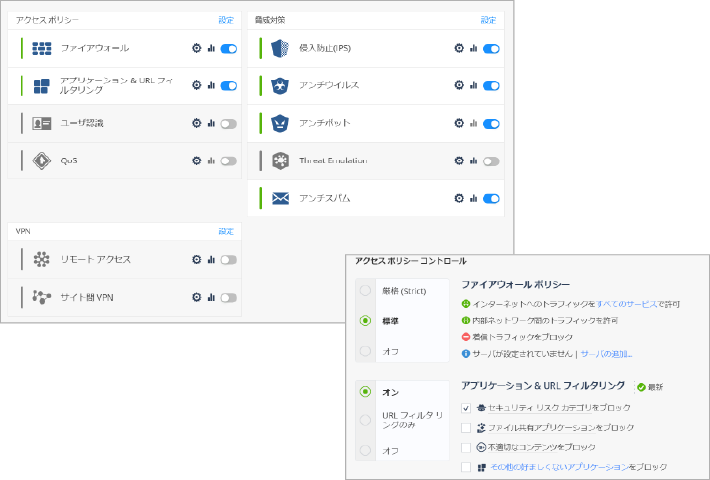
After enabling predefined security policies using the setup wizard, you can easily customize device settings and policies through the web-based management interface. Even UTM functions that are typically complex to configure can be quickly set to best-practice levels through an intuitive UI.
-
Built-in reporting for visibility into network threats
Despite its compact, low-cost desktop form factor, Quantum Spark includes rich, built-in reporting capabilities.
It visualizes network threats such as the number of detected malware instances, internet traffic and application usage, and the number of infected devices. Administrators can use automatically generated reports to easily understand the organization’s security posture and respond promptly to incidents.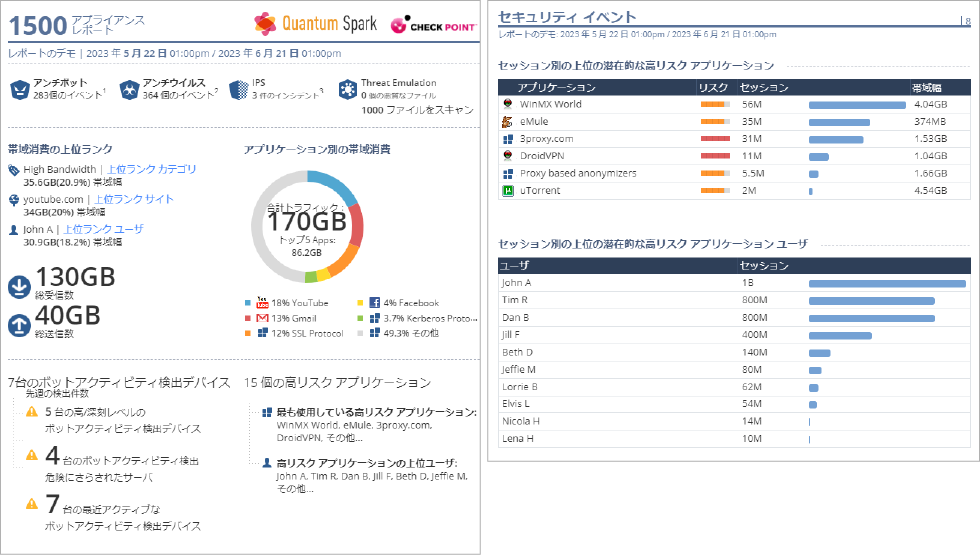
Deployment examples
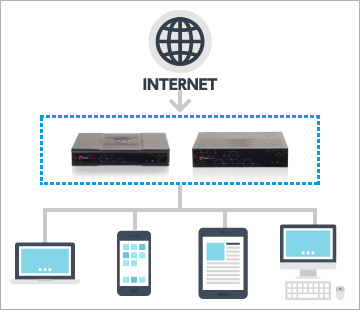
Deployment example 1: Gateway for small remote offices
- Uses Check Point security technologies trusted by Fortune 100 companies
- Provides comprehensive security features to continuously protect employee information and business data in small organizations
- Enables secure connectivity to the internal network from a wide variety of devices
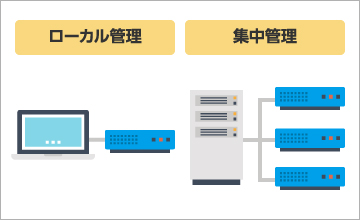
Deployment example 2: Managing branch gateways with best-in-class management
[Local management]
- Simple, web-based management interface for easy configuration
- Ability to customize device settings and policies after initial setup
- Clear logs and reports to manage device and security status
- Use a Security Management server to centrally define security policies across the entire network
- Apply consistent policies and visibility to all appliances
- Support for easy remote deployment using USB, even at branch locations
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
 Next-generation firewall for SMBs and mid-sized offices, delivering enterprise-grade security
Next-generation firewall for SMBs and mid-sized offices, delivering enterprise-grade security