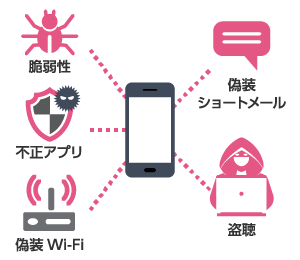
 Are you confident that your mobile devices are secure simply because they are “not lost” or because “application usage is restricted”?
Are you confident that your mobile devices are secure simply because they are “not lost” or because “application usage is restricted”?With the spread of SaaS and remote work, the use of mobile devices for business has accelerated, and at the same time, the risk of external access to critical internal data has increased.Attack vectors are becoming more diverse, including network and OS vulnerability exploits, phishing, and man-in-the-middle attacks using rogue Wi-Fi access points—threats that cannot be fully addressed by conventional antivirus apps alone.
In many Japanese companies, it is common to manage corporate mobile devices using MDM (Mobile Device Management). While MDM provides security features such as restricting the use of applications and performing remote wipe in case of loss, it cannot defend against the diversified attacks mentioned above.
Check Point Harmony Mobile from Check Point Software Technologies enables multifaceted protection using one of the industry’s largest threat intelligence platforms, covering these attacks as well as unknown malicious applications.
- Three layers of protection provided by Check Point Harmony Mobile
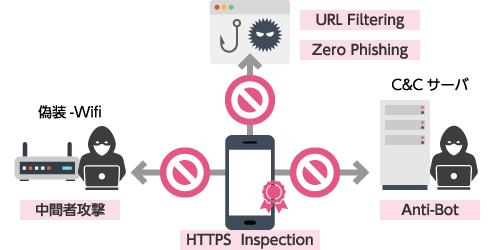
Network-level communication control and protection
Harmony Mobile blocks access to phishing sites. It restricts access to harmful content using URL filtering and protects against man-in-the-middle attacks via rogue Wi-Fi and access to C&C servers, defending against network-level attacks from multiple angles.
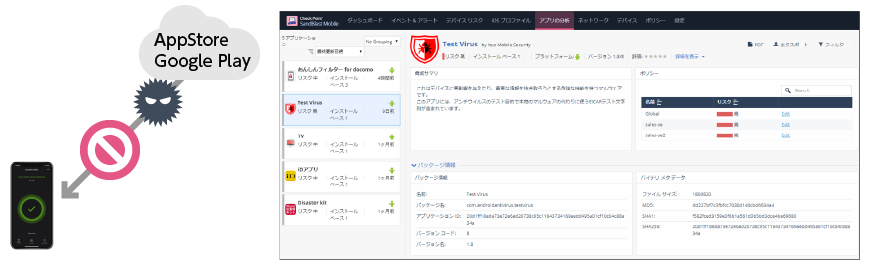
Protection against malicious applications
Using a cloud-based sandbox that performs threat intelligence and risk analysis, Harmony Mobile prevents malicious applications from infiltrating devices. Analysis results for applications can be viewed via a dedicated UI, and administrators can configure whitelists and blacklists.
Inspection and protection against mobile OS vulnerabilities
Harmony Mobile scans device configuration information such as OS version, applied patch levels, and jailbreak/root status. If a policy violation is found, it is reported as a risk.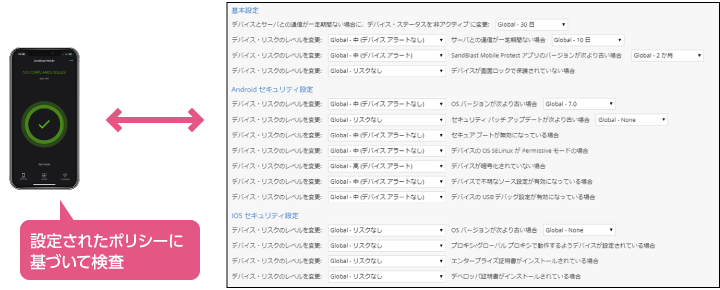
- Cloud-based management and threat-intelligence-driven ecosystem
Check Point Harmony Mobile is managed via a cloud-based portal. Its inspection engine uses “ThreatCloud,” a sandbox environment where static and dynamic analysis is performed to detect even unknown malware. ThreatCloud is the threat intelligence knowledge base also used by other Check Point Software Technologies products. It holds information on more than 500 million malware hashes and websites and is updated in real time through the detection of over 700,000 malware samples every day. While standalone products have limitations in terms of their own threat knowledge, Harmony Mobile achieves high detection rates for unknown malware and phishing sites through an ecosystem that shares threat intelligence across multiple Check Point products.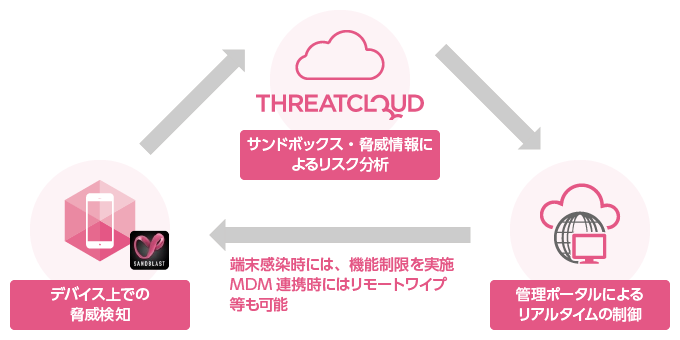
- Highly rated by independent evaluation organizations
Check Point Harmony Mobile has received high ratings from multiple independent evaluation organizations, including Gartner.
In a comparative test conducted by Miercom in 2019, it received the highest scores for factors such as protection effectiveness against threats, ease of use, ease of deployment, and cost.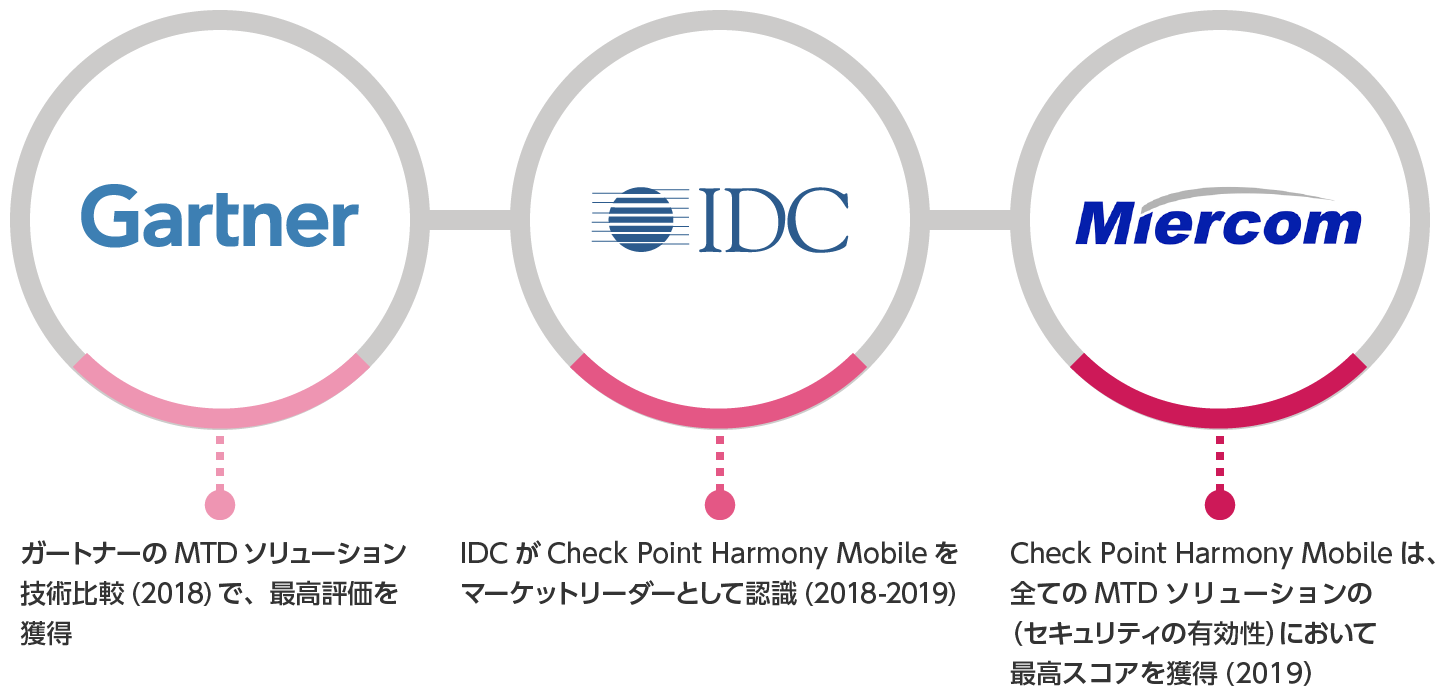
- Key points compared with MDM solutions
Check Point Harmony Mobile protects mobile devices against the latest security threats that cannot be mitigated by MDM alone.
Organizations that already use MDM can achieve stronger security and robust configuration management by adding and integrating Check Point Harmony Mobile on top of their existing MDM deployment.Security risk SandBlast Mobile MDM Lost Device Countermeasures (Remote Wipe) ✔ Device Encryption ✔ PIN (Passcode) Enforcement ✔ Restriction of Usable Applications ✔ JDetection of Jailbreak/Rooting ✔ Malware Detection (Known and Unknown) ✔ Phishing Detection (Known and Unknown) ✔ URL Filtering ✔ Wi-Fi Attack Detection ✔ C&C Communication Detection ✔ Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
- Cloud-based management and threat-intelligence-driven ecosystem
 An integrated mobile security solution that delivers multilayered protection against sophisticated mobile attacks
An integrated mobile security solution that delivers multilayered protection against sophisticated mobile attacks