Check Point Quantum Maestro is an easy-to-manage, hyper-scale network security solution. With a fundamentally different approach from conventional industry offerings, it maximizes the performance of your existing appliances without wasting prior hardware investments.
Key features of Check Point Quantum Maestro
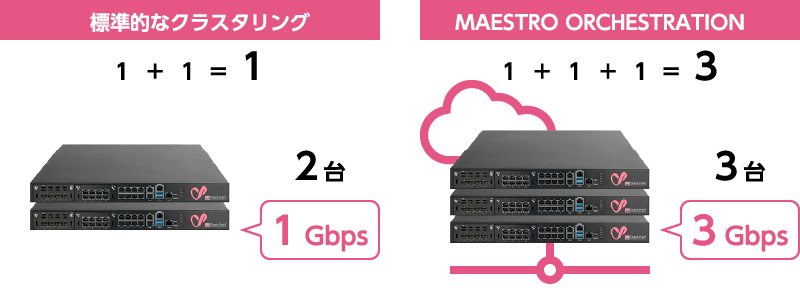
- Throughput increases as you add gateways
In a standard high-availability configuration, the gateways themselves handle connection synchronization and clustering, which makes it difficult to fully utilize appliance resources. Check Point Quantum Maestro instead calculates a hash value from the traffic and uses it to distribute packets across member gateways on their behalf. This allows the attached gateways to focus solely on traffic inspection, enabling you to draw out their maximum throughput.
-
Exceptional scalability—add gateways in just a few minutes
Check Point Quantum Maestro recognizes multiple gateways as a single logical system called a “Security Group.” When you add a gateway to a Security Group, all its settings, policies, and software versions are automatically aligned with the existing gateways. As a result, the new gateway is ready for production in about six minutes. This enables cloud-like scale-out capabilities in on-premises environments.
*Supported on models 6200 and above. A 10 Gbps expansion NIC is required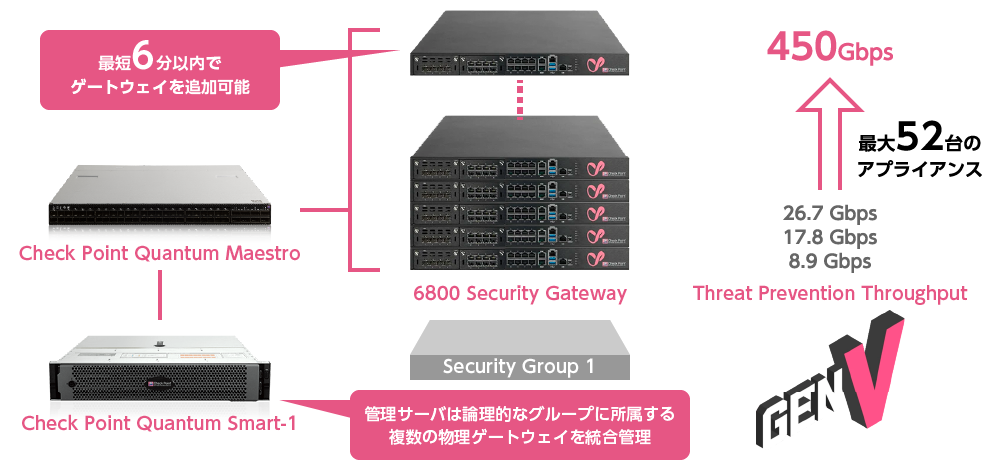
-
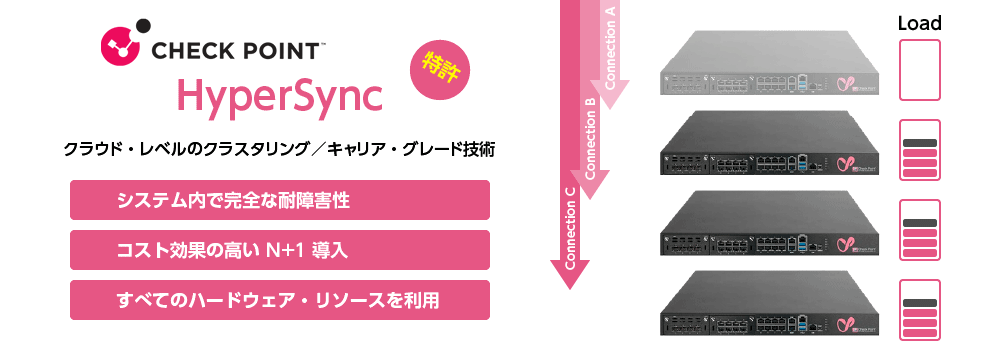
Cost-efficient, highly resilient N+1 clustering
Check Point Quantum Maestro uses a patented clustering technology called “HyperSync” to deliver carrier-grade fault tolerance.
HyperSync continuously tracks the status of member gateways and synchronizes traffic only with gateways that are handling active or standby connections. This reduces synchronization overhead and enables efficient N+1 clustering. If a gateway belongs to multiple Security Groups, resources can be dynamically reallocated; for example, shifting capacity from a lightly loaded group to another group experiencing high load—so that all hardware resources are used efficiently.
-
Deployment overview
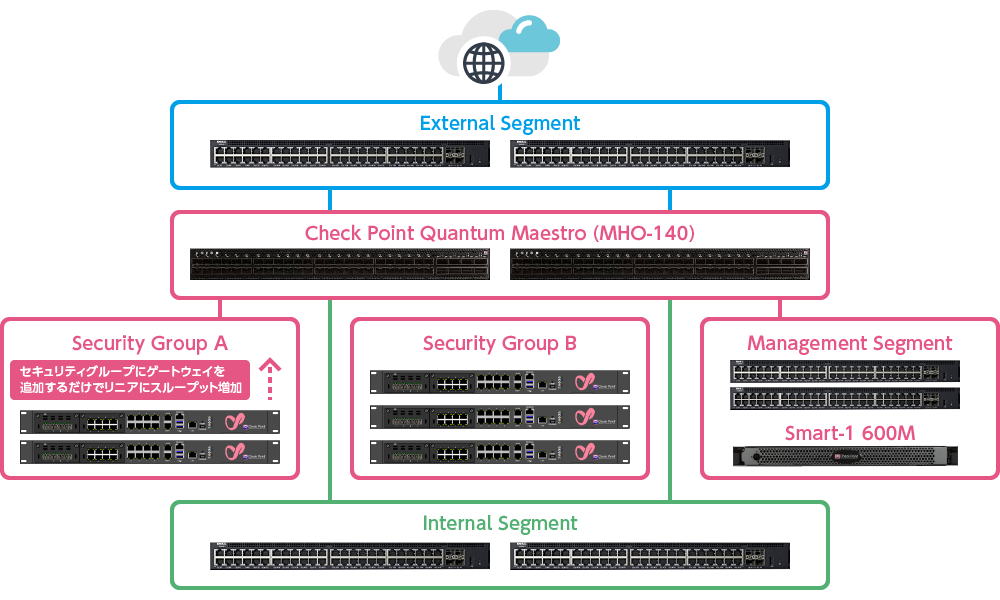
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management