 Protecting applications from a wide range of attacks
Application Protection
Protecting applications from a wide range of attacks
Application Protection
(formerly Arxan EnsureIT/GuardIT)
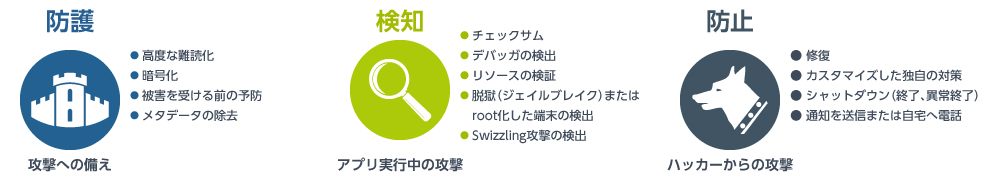
Digital ai. Application Protection is a product designed to protect applications from information leakage and the infringement of intellectual property theft caused by reverse engineering. It achieves this by hardening the code through “Guards”.
Code Hardening (Guards)
Application Protection supports multiple types of code hardening.
| Guard Type | Features | Use Cases |
|---|---|---|
| Debugger detection | Debugger Detection | Anti-Analysis Measures |
| Checksum | Tamper Detection | Anti-Tampering Measures |
| Code Obfuscation / Control Flow Obfuscation | Code Obfuscation | Anti-Analysis |
| Call hiding | Function Call Hiding | Anti-Analysis |
| Debug Info | Removal of Debug Information | Anti-Analysis |
| Class Encryption | Class Encryption | Anti-Analysis |
| Swizzling Detection | Swizzling Detection | Anti-Tempering modifications |
| Jailbreak Detection | Jailbreak Detection | Anti-Tempering |
| Root Detection | Root Detection | Anti-Tempering |
| Repair/Damage | Self-Repair & Self-Destruction | Anti-Tempering / Resilience |
| Renaming | Symbol Renaming | Anti-Tempering (Obfuscation) |
| Resource Verification | Resource Integrity Verification | Anti-Tempering |
| Resource Encryption | Resource Encryption | Anti-Analysis |
| String Encryption | String Encryption | Anti-Analysis |
| Data Obfuscation | Dynamic Data Obfuscation | Anti-Cheat / Anti-Analysis |
| Hook Detection | Hook Detection and API Integrity Check | Anti-Tempering |
| Emulator Detection | Emulator & Simulator Detection | Anti-Analysis |
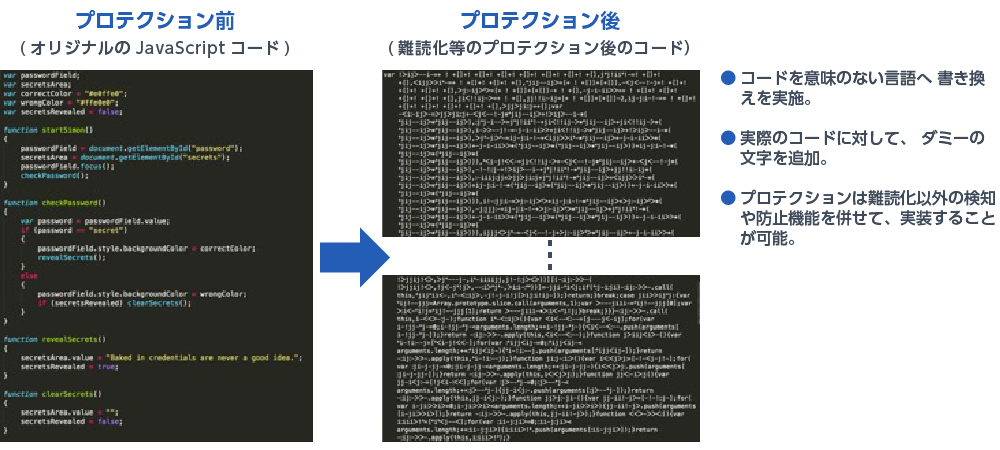
Code Obfuscation
After inline expansion, Application Protection applies randomly combined obfuscation algorithms at the assembly level to achieve highly sophisticated code obfuscation.
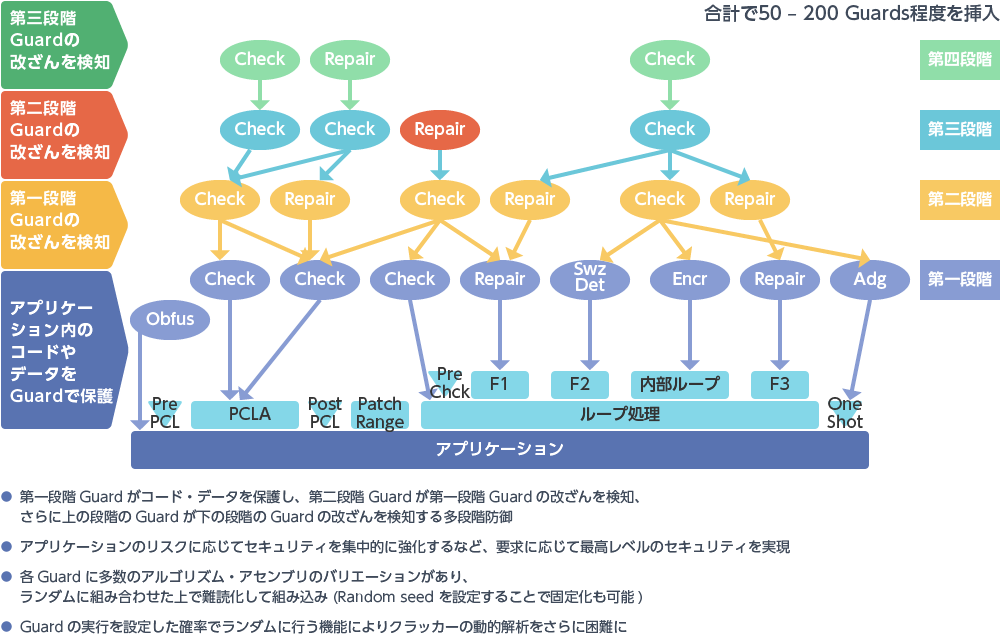
Multi-Layered Defense
Application Protection enables multi-layered defense by stacking checksums, encryption, and obfuscation.
By adopting a risk-based approach to intensigy protection where it is needed most, organizations can elevate their security posture to a grade resilient enough to neutralize sophisticated attacks from nation-state adversaries.
Security Products
- Next-Generation Firewall
- Targeted Attack Protection
- Cloud Security / Virtualization
- Mobile / Endpoint Security
- Email Security
- Anti-Phishing
(Business Email Compromise Protection, etc.) - Application Security
- Server Security
- Sandbox
- Malware Sanitization
- Log Analysis
- Server Monitoring
- Encryption
- Security Policy
- Industrial Control System Security
- Connected Car Security
- WAAP
- Browser Security
- Cloud Backup
- SASE
- Vulnerability Management
